Next.js is a powerful React framework widely used for building web applications due to its performance optimizations, server-side rendering (SSR), and seamless development experience. However, like any framework, it is not immune to security vulnerabilities. Recently, a critical security flaw (CVE-2025-29927) was disclosed, which could allow attackers to bypass authorization mechanisms under certain conditions. This blog post provides an in-depth explanation of the vulnerability, its implications, and how to mitigate the risks.
Table of Contents
Understanding Next.js Middleware and Security
What is Middleware in Next.js?
Middleware in Next.js is used to execute code before a request reaches a specific route. It enables various functionalities, such as:
Authentication and Authorization – Ensuring users have proper access.
Logging and Monitoring – Capturing request data for security and analytics.
Redirection – Sending users to different routes based on conditions.
Response Modification – Changing request headers or response payloads dynamically.
Middleware plays a crucial role in securing Next.js applications by validating requests before they reach sensitive routes.
The Role of x-middleware-subrequest
Next.js internally uses a special header, x-middleware-subrequest, to prevent recursive requests that could lead to infinite loops. This header ensures that middleware does not run multiple times on the same request, improving efficiency. However, the recent vulnerability exposed a flaw in its implementation.
CVE-2025-29927: The Next.js Authorization Bypass Vulnerability
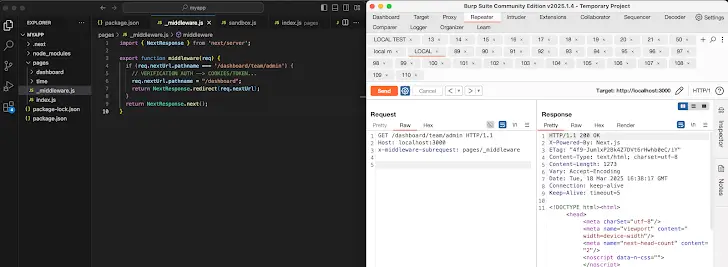
NextJS Middleware
What is CVE-2025-29927?
CVE-2025-29927 is a critical security flaw in Next.js that allows attackers to bypass middleware, including authentication and authorization checks, under certain conditions. This could lead to unauthorized access to protected resources, posing a severe security risk.
Severity and Impact
CVSS Score: 9.1/10 (Critical)
Affected Versions: Self-hosted instances using
next startwithoutput: standaloneUnaffected Deployments: Next.js applications hosted on Vercel, Netlify, or deployed as static exports
How the Exploit Works
Skipping Middleware Execution: By crafting specific requests, attackers can manipulate the
x-middleware-subrequestheader, effectively bypassing middleware execution.Authorization Bypass: Since authorization checks typically occur in middleware, skipping them allows attackers to gain unauthorized access.
Potential Consequences:
Unauthorized access to restricted user data.
Execution of API actions meant for authenticated users.
Potential exposure of sensitive application logic.
Also read on the additional technical details of the flaw
Mitigation Strategies: Handling the Situation
1. Upgrade to Patched Versions
The best way to secure your application is by upgrading to a patched Next.js version:
12.3.5
13.5.9
14.2.25
15.2.3
2. Prevent External Requests with x-middleware-subrequest Header
If upgrading is not immediately possible, apply the following security measure:
Block incoming requests that include the
x-middleware-subrequestheader to prevent unauthorized middleware skipping.Configure your web server (NGINX, Apache) or API gateway to reject such requests.
3. Strengthen Authorization at the API Level
Middleware-based authentication should not be the sole security mechanism. Implement:
Server-side authorization checks in API routes to prevent unauthorized actions.
Token-based authentication (JWT, OAuth) to validate every request securely.
4. Monitor Logs and Implement Security Alerts
Regularly monitor access logs for unusual requests or attempts to exploit the vulnerability.
Implement anomaly detection tools to flag suspicious behavior.
Conclusion
CVE-2025-29927 is a serious security vulnerability that highlights the importance of robust middleware implementation and security best practices in Next.js applications. By understanding the exploit, upgrading to patched versions, and implementing additional security measures, developers can safeguard their applications against unauthorized access. Stay proactive, monitor your applications, and always follow best security practices to mitigate such risks in the future.
For more insights on securing your Next.js applications, keep an eye on official security advisories and community updates.
References
Why Businesses Trust SecureMyOrg for Comprehensive Network Security
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!







Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Relevant Posts

Critical Zero-Day in FortiVoice Patched by Fortinet After Active Exploits
Fortinet has patched a critical zero-day vulnerability (CVE-2025-32756) exploited in active attacks targeting FortiVoice and other products like FortiMail and FortiCamera. The flaw allowed remote code execution via crafted HTTP requests, with attackers deploying malware and harvesting credentials before the fix was released.

Top 5 Cloud-Focused Remote Access Trojans in 2025
Cloud environments are prime targets in 2025, with Remote Access Trojans engineered specifically to exploit them. This blog covers the top 5 cloud-focused RATs causing major security concerns.

Top 5 Fileless Remote Access Trojans in 2025
Fileless Remote Access Trojans are redefining stealth attacks in 2025 by leaving little to no trace on disk. This blog explores the top 5 fileless RATs attackers are using today.

Dissecting AsyncRAT’s Hold on Windows Systems in 2025
AsyncRAT continues to dominate Windows system compromises in 2025 with its stealth and modular design. This post dissects how it operates and why it remains a persistent threat.

Top 5 IoT Remote Access Trojans Crippling Devices in 2025
IoT devices are under siege in 2025 as Remote Access Trojans exploit their vulnerabilities at scale. This blog breaks down the top 5 IoT RATs causing widespread disruption.
Top 5 Web-Based Remote Access Trojans That Are Dominating 2025
Web-based Remote Access Trojans are becoming the go-to tool for cybercriminals in 2025. This post highlights five of the most widespread and dangerous ones currently in use.

