We live in a digital age, and securing sensitive information is more important than ever. Between the two main types of encryption, symmetric encryption stands out for its simplicity and efficiency. In this article, we will explore the concept of symmetric encryption, how it works, its advantages, and its limitations, providing a clear understanding of this fundamental aspect cryptography.
Table of Contents
What is Symmetric Encryption?
Symmetric encryption, often referred to as secret-key encryption, is a method where the same key is used for both encryption and decryption. This approach ensures that only those possessing the secret key can access the encrypted data. It is widely used in various applications due to its speed and efficiency, making it an ideal choice for encrypting large amounts of data.
Key Components of Symmetric Encryption:
- Plaintext: The original, unencrypted data.
- Ciphertext: The encrypted version of the data.
- Encryption Algorithm: The mathematical process used to transform plaintext into ciphertext.
- Key: A string of characters used to encode and decode data.
How Symmetric Encryption Works
To understand symmetric encryption, let’s break down the process into simple steps:
Encryption:
- The plaintext data is input into the encryption algorithm along with a secret key.
- The algorithm transforms the plaintext into ciphertext, making it unreadable without the key.
Decryption:
- The ciphertext is input into the same algorithm, this time with the secret key to revert it to plaintext.
- Without the correct key, the data remains unintelligible.
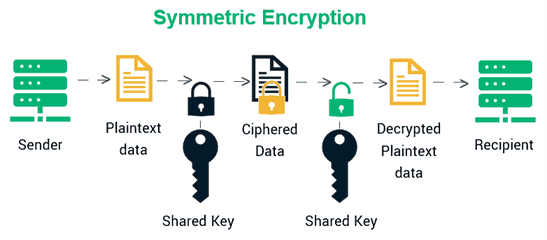
Diagram: The Symmetric Encryption Workflow
Let’s visualize the workflow through a simple diagram:
- Plaintext → Encryption Algorithm + Secret Key → Ciphertext
- Ciphertext → Decryption Algorithm + Secret Key → Plaintext
Symmetric Encryption Workflow
Symmetric Encryption Algorithms
Symmetric encryption algorithms are cryptographic techniques that use the same key for both the encryption and decryption processes. These algorithms are designed to be fast and efficient, making them ideal for encrypting large volumes of data.
Common examples of symmetric encryption algorithms include:
- AES (Advanced Encryption Standard): A widely used algorithm known for its high security and efficiency.
- DES (Data Encryption Standard): An older algorithm that is now considered insecure due to its short key length.
- 3DES (Triple DES): An improvement on DES that applies the algorithm three times for added security.
- Blowfish and Twofish: Algorithms designed for high performance, often used in file encryption and secure communication.
The main advantage of symmetric encryption is its speed, but a major challenge is the secure distribution of the key between the sender and the recipient. If the key is intercepted or exposed, the security of the entire encryption process is compromised.
Pros and Cons of Symmetric Encryption
| Pros | Cons |
|---|---|
| Fast and efficient for large amounts of data. | Key management can be challenging; the same key must be securely shared between parties. |
| Less computational overhead compared to asymmetric encryption. | If the key is compromised, all data encrypted with that key is at risk. |
| Widely used and supported in various applications and protocols. | Does not provide authentication; requires additional methods to verify the identity of parties. |
| Simple implementation and understanding of the encryption process. | Scalability issues arise as the number of users increases; each pair needs a unique key. |
Pros:
When it comes to encrypting large volumes of data quickly and efficiently, symmetric encryption shines as one of the most powerful cryptographic tools. Here are some of its major advantages.
- Speed: Compared to asymmetric encryption, symmetric methods are faster, making them suitable for encrypting large datasets.
- Simplicity: Using a single key reduces the complexity of the encryption process.
- Low Resource Consumption: It requires fewer computational resources, making it ideal for devices with limited processing power.
While efficient, symmetric encryption requires careful handling of keys, as its reliance on a single shared key introduces potential vulnerabilities.
Cons:
- Key Distribution: Securely sharing the secret key between parties can be challenging.
- Scalability: In environments with multiple users, managing keys becomes complex.
- No Non-repudiation: Symmetric encryption does not provide proof of the sender’s identity, as both parties use the same key.
Symmetric vs Asymmetric Encryption
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Usage | Same key for encryption and decryption | Different keys (public and private) |
| Speed | Faster | Slower |
| Security Level | Dependent on key management | Higher due to key pair |
| Key Distribution | Challenging | Easier (public keys can be shared openly) |
The table compares symmetric encryption and asymmetric encryption across four key aspects:
Key Usage:
- Symmetric encryption uses the same key for both encryption and decryption, whereas asymmetric encryption uses a pair of keys—a public key for encryption and a private key for decryption.
Speed:
- Symmetric encryption is faster, making it ideal for large datasets. In contrast, asymmetric encryption is slower due to the complexity of its algorithms.
Security Level:
- Symmetric encryption’s security depends on effective key management. Asymmetric encryption provides higher security through the use of key pairs.
Key Distribution:
- Sharing keys in symmetric encryption is challenging, as the secret key must remain confidential. Asymmetric encryption simplifies this by allowing public keys to be openly shared while keeping private keys secure.
Common Use Cases for Symmetric Encryption
Despite its limitations, symmetric encryption remains a vital tool in the cryptography world. While challenges such as key distribution and scalability exist, these issues can often be mitigated through proper key management strategies and hybrid encryption systems. Let’s explore some of its common use cases:
- File Encryption: Protecting sensitive files stored on a computer or cloud storage.
- Network Security: Ensuring secure communication over networks using protocols like SSL/TLS.
- Payment Systems: Encrypting transaction details in financial applications.
- Database Encryption: Safeguarding sensitive records in databases.
Enhancing Symmetric Encryption
To address its limitations, symmetric encryption is often used alongside other cryptographic methods. For instance:
- Hybrid Encryption Systems: Combining symmetric encryption (for speed) with asymmetric encryption (for secure key exchange).
- Key Management Systems: Automating key generation, storage, and sharing to reduce risks.
Conclusion
Symmetric encryption remains an essential tool in the cryptography toolkit. Its balance of speed and simplicity makes it ideal for many applications, from securing personal files to protecting sensitive business transactions. However, understanding its limitations and combining it with complementary technologies ensures a comprehensive approach to data security.
In an era where cyber threats continue to evolve, symmetric encryption’s role in safeguarding information is more important than ever. By mastering its principles and best practices, individuals and organizations can take significant strides toward enhanced security.
About SecureMyOrg
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!
Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.