Burp Suite is a vital tool for professionals seeking to identify vulnerabilities in web applications. Developed by PortSwigger, Burp Suite offers a comprehensive set of tools for web application security testing, making it the go-to choice for penetration testers worldwide. Whether you are a beginner or a seasoned professional, mastering Burp Suite can significantly enhance your capabilities. This ultimate guide aims to walk you through everything you need to know about using Burp Suite effectively.
Table of Contents
What Is Burp Suite?

Burp Suite is a top penetration testing tool designed for web application security testing. It provides a suite of features, ranging from intercepting HTTP traffic to advanced vulnerability scanning and reporting. The tool is available in three editions:
Community Edition: Free but limited in features. Best suited for beginners.
Professional Edition: A paid version offering advanced capabilities like automated vulnerability scanning.
Enterprise Edition: Designed for large-scale scanning and enterprise environments.
Why Use Burp Suite?
Burp Suite is renowned for its versatility and user-friendly interface. Its key features include:
Intercepting Proxy: Captures and modifies HTTP and HTTPS traffic between your browser and the web server.
Scanner: Identifies common vulnerabilities such as SQL injection, cross-site scripting (XSS), and more.
Intruder: Automates custom attacks to test for weaknesses.
Repeater: Allows manual testing of specific requests.
Decoder: Decodes data in various formats.
Comparer: Compares two pieces of data to identify differences.
Extensibility: Supports custom plugins through the Burp Extender API.
Getting Started with Burp Suite
1. Installation and Setup
To begin, download Burp Suite from the official PortSwigger website. Install the application and set up your browser to route traffic through Burp’s proxy. This typically involves:
Configuring the browser to use Burp Suite’s proxy server.
Installing Burp’s CA certificate to intercept HTTPS traffic securely.
2. Familiarize Yourself with the Interface
The main components of Burp Suite are accessible through its tabbed interface:
Dashboard: Provides an overview of project activity.
Target: Displays details of the target application.
Proxy: Allows you to intercept and inspect HTTP traffic.
Scanner: Automates vulnerability detection (Professional and Enterprise editions only).
Intruder: Useful for brute force attacks and parameter fuzzing.
Repeater: Enables manual request testing.
Extender: Manages extensions to enhance functionality.
Using Burp Suite for Web Application Penetration Testing
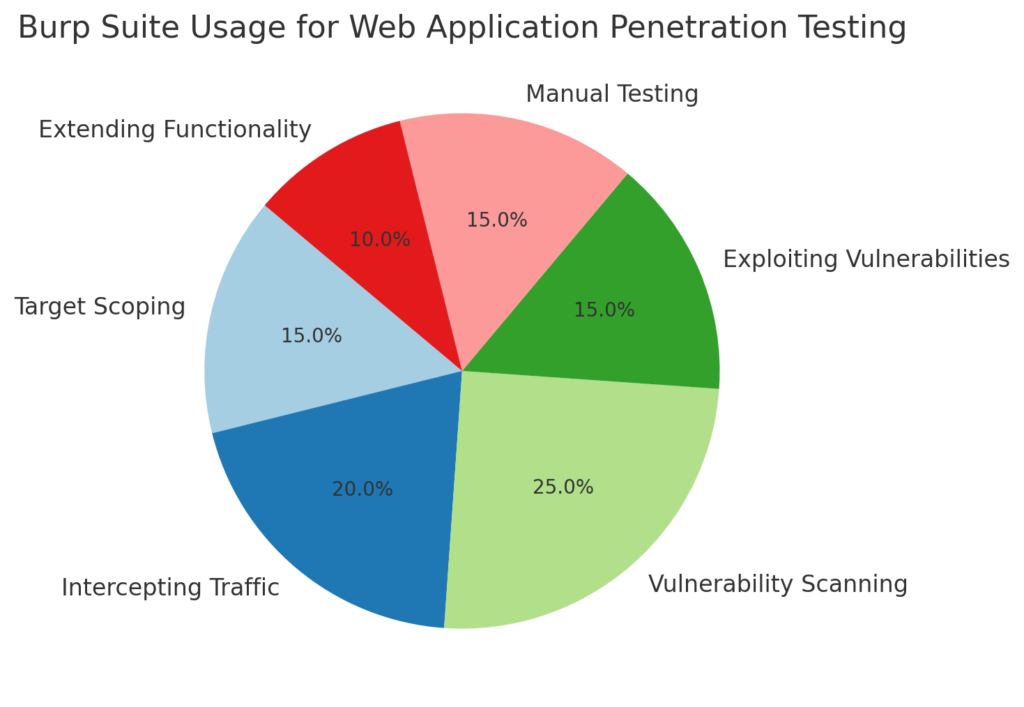
1. Target Scoping
Before starting any testing, define your scope to focus only on authorized targets. This helps prevent accidental testing on unintended domains, which can lead to legal consequences. Use the “Scope” feature in the Target tab to specify which URLs should be tested.2. Intercepting Traffic
Burp Suite’s Proxy tool is the first step in analyzing a web application. By intercepting traffic, you can:- Inspect HTTP requests and responses.
- Modify data in transit to test input validation.
- Identify hidden parameters.
3. Vulnerability Scanning
For those using the Professional edition, Burp Suite’s Scanner automates the detection of common vulnerabilities. Configure the scanner to focus on areas of interest, such as:- SQL Injection
- Cross-Site Scripting (XSS)
- Broken Authentication
4. Exploiting Vulnerabilities with Intruder
The Intruder tool is ideal for testing specific vulnerabilities, such as weak passwords or input-based attacks. Configure the Intruder by:- Setting target positions within the HTTP request.
- Selecting a payload (e.g., a wordlist for brute force attacks).
- Adjusting attack types (e.g., Sniper, Battering Ram, Pitchfork, Cluster Bomb).
5. Manual Testing with Repeater
The Repeater tool is a favorite among professionals for manual testing. By modifying and resending requests, you can:- Test input fields for SQL Injection or XSS.
- Analyze server responses.
- Confirm vulnerabilities identified by automated tools.
6. Extending Burp Suite’s Functionality
Leverage Burp Extensions to customize and enhance Burp Suite. Popular extensions include:- Logger++: Provides detailed logging of HTTP requests and responses.
- JSON Beautifier: Simplifies the analysis of JSON data.
- Active Scan++: Enhances the capabilities of the default Scanner.
Best Practices for Using Burp Suite
1. Understand the Application
Take time to map out the application’s functionality. Use Burp Suite’s Target tab to identify endpoints, directories, and parameters.
2. Stay Ethical
Always obtain proper authorization before testing. Follow legal and ethical guidelines to avoid unintended consequences.
3. Optimize Performance
Burp Suite can be resource-intensive. Optimize performance by:
Adjusting the number of threads for automated scans.
Excluding large or irrelevant files (e.g., images, videos) from the scope.
4. Keep Learning
Cybersecurity is a rapidly evolving field. Stay updated on the latest techniques and vulnerabilities by exploring resources like the OWASP Top Ten and participating in bug bounty programs.
Conclusion
Mastering Burp Suite requires practice and a deep understanding of web application security. By leveraging its powerful features, you can identify and exploit vulnerabilities effectively. Remember, ethical hacking is about protecting systems and ensuring safety. Use Burp Suite responsibly, and you’ll be well on your way to becoming a cybersecurity expert.
Whether you’re preparing for a penetration test or participating in a bug bounty program, Burp Suite is an indispensable tool. With this guide, you now have the foundational knowledge to start mastering Burp Suite. Happy testing!
Why Businesses Trust SecureMyOrg for Comprehensive Network Security
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!







Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.
