In January 2025, cybersecurity researchers disclosed a critical security vulnerability identified as CVE-2025-21298, affecting Windows Object Linking and Embedding (OLE) technology. This flaw has been assigned a CVSS score of 9.8, indicating its severe impact and high exploitability. If successfully exploited, attackers can execute remote code (RCE) on a target system simply by sending a specially crafted email, posing a massive threat to individuals and organizations.
Given the widespread use of Windows OLE in applications like Microsoft Office and Outlook, this vulnerability presents a significant risk for phishing-based attacks. Attackers can embed malicious content in email attachments or documents, allowing them to bypass security defenses and gain unauthorized access.
In this blog, we’ll explore the technical details of CVE-2025-21298, how it can be exploited, and the best practices for mitigating the risk before it leads to widespread cyberattacks.
What is CVE-2025-21298?
CVE-2025-21298 is a critical security vulnerability in Windows OLE, a technology that enables applications like Microsoft Outlook to embed and link documents, spreadsheets, and other objects. The vulnerability allows attackers to execute arbitrary code on a victim’s system without requiring any user interaction beyond opening or previewing a malicious email.
CVE-2025-21298: Breaking it Down
- Severity (CVSS score 9.8/10) – A 9.8 score indicates an extremely severe issue, almost the highest possible, suggesting it is easily exploitable and has severe consequences.
- Vulnerability Type – Remote Code Execution (RCE) – Attackers can exploit this flaw to execute arbitrary code on a target system remotely without the victim’s consent.
- Exploitation Method – Specially Crafted Emails – This suggests that the vulnerability can be triggered by simply opening or previewing a malicious email, making it a phishing-based attack vector.
- Affected Technology – Windows OLE – OLE (Object Linking and Embedding) is a Microsoft technology that allows embedding and linking documents (e.g., Excel inside Word). If OLE is exploited, it could allow malicious payloads to run automatically.
CVE-2025-21298: A Deep Dive into the Technical Flaw
The vulnerability exists within ole32.dll, specifically in the UtOlePresStmToContentsStm function. This function is responsible for converting data within an “OlePres” stream into the appropriate format and inserting it into the “CONTENTS” stream inside an OLE storage structure. However, due to improper memory handling during this conversion process, a memory corruption issue occurs, making it possible for attackers to execute arbitrary code on the affected system.
A proof-of-concept (PoC) exploit for CVE-2025-21298 has already been published on GitHub, showcasing how this flaw can be leveraged to achieve remote code execution. This PoC highlights the severity of the vulnerability, demonstrating how an attacker can craft a malicious OLE object that triggers memory corruption and leads to system compromise.
Demonstrating how the Attack Works
Step-by-Step Exploitation Process
To understand how CVE-2025-21298 is exploited, security researchers have demonstrated a Proof-of-Concept (PoC) attack that triggers the vulnerability in Windows Object Linking and Embedding (OLE). Here’s a breakdown of how the attack works in a controlled environment:
Launching Microsoft Word
- The attacker (or researcher) opens a new instance of Microsoft Word on a vulnerable Windows system.
- This sets up the environment where OLE processing occurs.
image attribute: Offsec.com blog
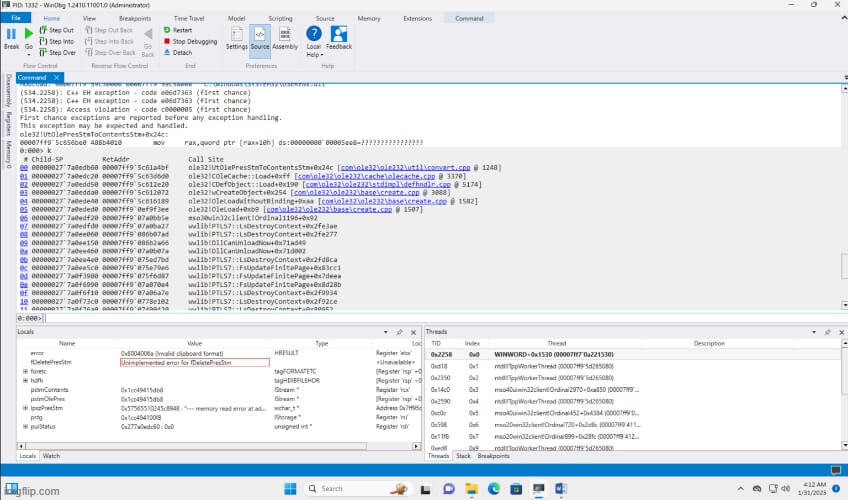
Attaching a Debugger
- The next step is to attach WinDbg (Windows Debugger) to the running
WINWORD.EXEprocess. - This allows monitoring of memory interactions and crash behaviors when the exploit is triggered.
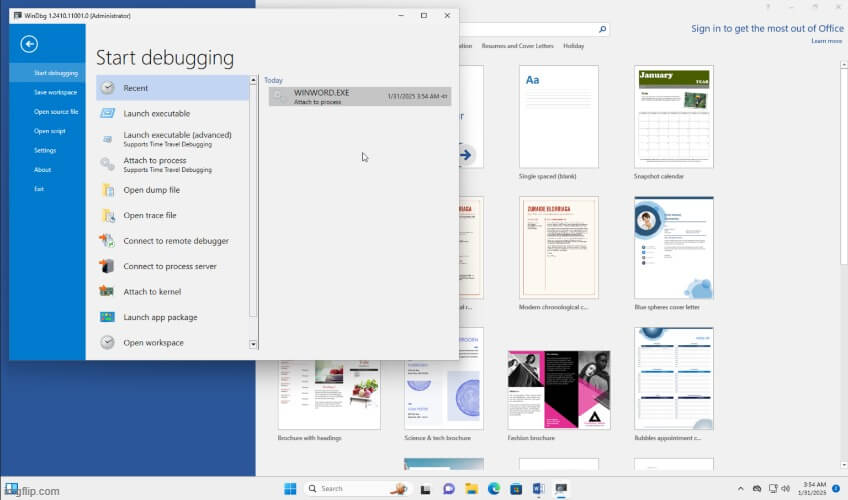
-attaching a debugger
Opening the Malicious RTF File
- The attacker opens a specially crafted
.rtffile (PoC exploit) within Microsoft Word. - This malicious RTF document, available in the GitHub PoC repository, contains embedded OLE content designed to exploit the vulnerability.
- The attacker opens a specially crafted
Triggering the Crash
- As soon as Word processes the malicious OLE object within the RTF file, it attempts to convert data using the vulnerable
UtOlePresStmToContentsStmfunction inole32.dll. - Due to memory corruption in this function, Word crashes—a strong indication of a successful exploitation attempt.
- In a real-world attack scenario, this could lead to remote code execution (RCE), allowing attackers to execute arbitrary commands on the victim’s system.
- As soon as Word processes the malicious OLE object within the RTF file, it attempts to convert data using the vulnerable
Why is This Vulnerability Dangerous?
Zero-Click Exploitation:
Unlike many vulnerabilities that require user interaction (e.g., clicking a link or opening an attachment), this flaw can be triggered simply by previewing the email. This makes it highly effective and difficult to detect.Widespread Impact:
Windows OLE is a core technology used in many Microsoft applications, including Outlook. This means the vulnerability could affect millions of users worldwide.Arbitrary Code Execution:
The ability to execute arbitrary code gives attackers the power to install malware, steal sensitive data, or further compromise the system.
Who is at Risk?
Microsoft Outlook Users: Anyone using Outlook to manage their emails is at risk, especially if they preview emails without caution.
Organizations: Businesses relying on Microsoft products for communication and document management are particularly vulnerable, as attackers could target employees to gain access to corporate networks.
Individuals: Personal users who receive emails from unknown or untrusted sources could also be affected.
Mitigation and Best Practices
1. Apply Security Patches
Microsoft has released patches to address this vulnerability as part of their January 2025 Patch Tuesday updates. Users and organizations are strongly advised to install these updates immediately to prevent exploitation.
2. Temporary Workarounds for Unpatched Systems
For systems that cannot be updated immediately, the following workarounds can help reduce the risk:
- Configure Outlook to read all emails in plain text format. This prevents malicious OLE objects in RTF or HTML emails from being processed automatically.
- Disable OLE in Microsoft Office applications using Group Policy settings to prevent embedded objects from being executed.
- Restrict execution of RTF files by modifying registry settings to prevent Word from opening them automatically.
3. Strengthening Security Defenses
Organizations should implement additional security controls:
- Use Endpoint Protection Solutions – Deploy advanced security software to detect and block malicious RTF or Office documents.
- Enable Email Filtering – Configure mail servers to block or quarantine emails containing suspicious OLE objects.
- Conduct Cybersecurity Awareness Training – Educate employees on phishing threats and document-based malware attacks.
- Implement Network Segmentation – Reduce the spread of an attack by limiting access to critical systems.
By following these mitigation strategies, users can significantly reduce the risk of falling victim to CVE-2025-21298 exploits.
References
- CVE-2025-21298: Critical OLE vulnerability in Windows-SOC Prime
- CVE-2025-21298: Windows OLE remote code execution vulnerabilty-Integrity360
Also read other CVE’s: - PWN-request vulnerability in stripe’s repo -SecureMyOrg
- Git RCE – CVE 2024-32002 | Technical Walkthrough & Recreating The Bug Locally -SecureMyOrg
Conclusion
CVE-2025-21298 represents a major security threat due to its ability to facilitate remote code execution through Microsoft OLE technology. With a CVSS score of 9.8, it is one of the most critical vulnerabilities disclosed in 2025, allowing attackers to compromise systems through malicious email attachments.
Microsoft has released patches to fix this flaw, and users must apply these updates immediately to secure their systems. For those unable to update, workarounds such as disabling OLE and configuring Outlook to read emails in plain text can provide temporary protection.
As attackers continue to develop sophisticated methods for exploiting vulnerabilities, staying proactive with software updates, security configurations, and employee training is crucial. Cybersecurity is a shared responsibility, and taking the right precautions can help prevent potential attacks.
Why Businesses Trust SecureMyOrg for Comprehensive Network Security
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!







Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.
