Symmetric encryption and asymmetric encryption are two of the most widely used encryption methods. Each method has its unique strengths and limitations, especially when it comes to performance. In this article, we’ll compare symmetric and asymmetric encryption, exploring their differences, use cases, and performance characteristics.
Table of Contents
Symmetric encryption is one of the oldest and simplest forms of data encryption. It uses a single key for both the encryption and decryption processes. The same key is shared between the sender and the recipient, making it essential for both parties to keep it confidential. Examples of symmetric encryption algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES).
How Symmetric Encryption Works
- The sender uses a secret key to encrypt the plaintext into ciphertext.
- The ciphertext is sent over a potentially insecure channel.
- The receiver uses the same secret key to decrypt the ciphertext back into plaintext.
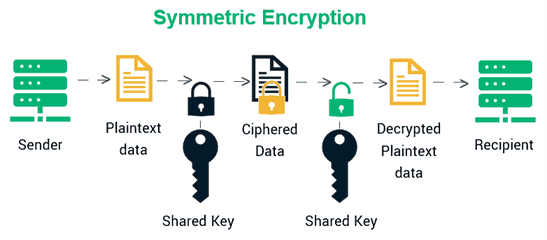
Since symmetric encryption uses the same key for both encryption and decryption, it is generally faster than asymmetric encryption. The performance advantage is due to the algorithm’s relatively straightforward mathematical operations, which require less computational power.
Pros and Cons of Symmetric Encryption
Pros:
- Speed: Symmetric encryption is significantly faster than asymmetric encryption, especially when dealing with large volumes of data.
- Efficiency: It requires less computational power, making it ideal for encrypting bulk data or real-time applications like video streaming and online gaming.
- Simplicity: The algorithms are simpler and easier to implement.
Cons:
- Key distribution: Sharing the secret key securely between parties can be challenging, especially over public networks.
- Scalability issues: For a network with many users, a unique key must be shared between each pair of users, which can become cumbersome to manage.
- Security risk: If the key is compromised, all communication encrypted with that key is vulnerable.
Understanding Asymmetric Encryption
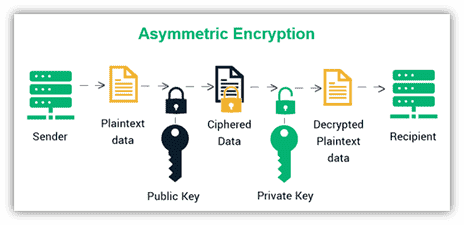
Asymmetric encryption, also known as public-key encryption, uses two different keys: a public key for encryption and a private key for decryption. The public key is openly shared, while the private key remains confidential to its owner. Popular asymmetric encryption algorithms include RSA (Rivest–Shamir–Adleman), Elliptic Curve Cryptography (ECC), and Digital Signature Algorithm (DSA).
How Asymmetric Encryption Works
- The sender uses the recipient’s public key to encrypt the plaintext into ciphertext.
- The encrypted message is sent over the network.
- The recipient uses their private key to decrypt the ciphertext back into plaintext.
Pros and Cons of Asymmetric Encryption
Pros:- Enhanced security: The private key is never shared, making it highly secure against interception.
- Key distribution: There is no need to exchange secret keys, reducing the risk of compromise.
- Scalability: Asymmetric encryption is more scalable since only public keys need to be distributed.
- Performance: Asymmetric encryption is significantly slower than symmetric encryption, making it less suitable for encrypting large amounts of data.
- Resource-intensive: It requires more computational power, which can be a concern for devices with limited processing capabilities.
- Complexity: Implementing asymmetric encryption systems can be more complex and costly.
Comparing Asymmetric and Symmetric Encryption Performance
With a clear understanding of how symmetric and asymmetric encryption function, we can now focus on the main aspect: performance.
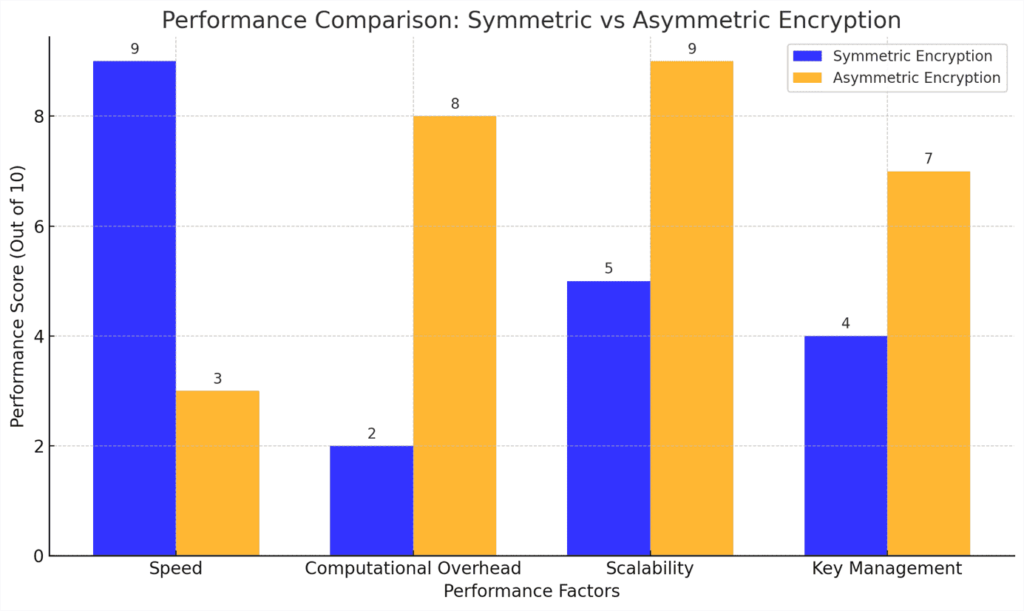
The performance differences between symmetric and asymmetric encryption are primarily due to the underlying mathematical operations. Let’s compare their performance in terms of speed, computational overhead, and scalability.
1. Speed and Efficiency
Symmetric encryption is much faster than asymmetric encryption because it uses simpler algorithms. For instance, AES encryption is known to be up to 1000 times faster than RSA encryption. The speed advantage of symmetric encryption makes it ideal for encrypting large files or streaming data where performance is critical. Asymmetric encryption, on the other hand, is more suited for scenarios where security is more important than speed, such as encrypting passwords, digital signatures, or securing key exchanges.
Performance Benchmark:
- AES (Symmetric): Capable of encrypting data at a speed of several gigabits per second.
- RSA (Asymmetric): Generally encrypts data at a rate of only a few kilobits per second due to the computational complexity of its algorithm.
2. Computational Overhead
The complexity of asymmetric encryption stems from the use of large prime numbers and modular exponentiation, which require substantial computational resources. Symmetric encryption algorithms like AES, in contrast, rely on simpler operations such as substitutions, permutations, and shifting bits, resulting in much lower computational overhead. For this reason, asymmetric encryption is typically used for smaller data sizes, like exchanging keys, while symmetric encryption is used for bulk data encryption.
3. Scalability
In a system where multiple users need to communicate securely, symmetric encryption can become unwieldy since each pair of users requires a unique shared key. In contrast, asymmetric encryption scales more efficiently because it only requires the distribution of public keys, which do not need to be kept secret. However, the scalability of asymmetric encryption comes at the cost of performance.
Common Use Cases of Symmetric and Asymmetric Encryption
Understanding the performance characteristics of both encryption types can help determine their suitability for different use cases:
- Symmetric Encryption:
- File encryption: Protecting data stored on devices.
- Virtual Private Networks (VPNs): Ensuring secure communication over public networks.
- Streaming services: Encrypting high-bandwidth content in real-time.
- Asymmetric Encryption:
- Secure key exchange: Used in protocols like TLS/SSL to exchange symmetric keys securely.
- Digital signatures: Authenticating the identity of a sender and ensuring the integrity of a message.
- Email encryption: Encrypting sensitive email content with PGP (Pretty Good Privacy).
| Aspect | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Speed | Extremely fast; can encrypt large files in seconds | Significantly slower; ideal for small data |
| Computational Overhead | Low; minimal CPU usage | High; requires substantial processing power |
| Scalability | Less scalable; needs unique keys for each connection | Highly scalable; only public keys need to be shared |
| Key Management | Challenging; secure key exchange is necessary | Simpler; no need to exchange private keys |
| Best Use Case | Large data encryption, streaming, and real-time applications | Digital signatures, secure key exchange, email encryption |
Combining Symmetric and Asymmetric Encryption: "The Best of Both Worlds"
In practice, many secure communication protocols leverage a hybrid approach, combining both symmetric and asymmetric encryption to optimize performance and security. For instance, the TLS/SSL protocol used in securing web traffic uses asymmetric encryption to exchange a symmetric session key. Once the session key is securely exchanged, it is used for faster symmetric encryption of data throughout the session.
This hybrid model addresses the weaknesses of both systems: it benefits from the efficiency of symmetric encryption while leveraging the security advantages of asymmetric encryption for key exchange.
Conclusion
In the debate between symmetric and asymmetric encryption, there is no clear winner since each method has its strengths and is better suited for specific applications. Symmetric encryption excels in scenarios that require high-speed data processing, such as bulk data transfer or real-time communication, thanks to its efficiency and low overhead. Meanwhile, asymmetric encryption is ideal for situations where security and key management are of utmost importance, such as secure key exchanges and digital signatures.
For most practical applications, a hybrid approach that combines the best of both worlds is often the preferred solution, ensuring robust security without sacrificing performance. As cyber threats continue to evolve, understanding the nuances of these encryption techniques will remain essential for protecting sensitive information and maintaining trust in digital communications.
About SecureMyOrg
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!
Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.
