Code-signing certificates are a cornerstone of software security, verifying that an application comes from a legitimate source and hasn’t been tampered with. However, cybercriminals have long exploited these certificates to sign malware, making malicious files appear trustworthy to security systems.
Microsoft’s Trusted Signing service, launched in 2024, was designed to simplify code-signing for developers. Unfortunately, attackers have found ways to abuse this service, using it to sign malware and bypass security defenses like SmartScreen and antivirus software.
In this blog, we’ll explore how cybercriminals are misusing Microsoft’s Trusted Signing, the real-world malware campaigns leveraging this method, and what organizations can do to defend against these threats.
Table of Contents
What is a Code Sign-in Malware?
Code Sign-In Malware is a type of malicious software that exploits legitimate code-signing certificates to bypass security defenses and appear trustworthy. Code-signing is a process where software developers sign their code with a digital certificate, verifying its authenticity and integrity. However, cybercriminals can steal or fraudulently obtain these certificates to sign their malware, making it seem like a legitimate application.
The Role of Code-Signing Certificates in Cybersecurity
Code-signing certificates act as digital signatures, confirming that software comes from a verified publisher and hasn’t been altered. Security systems, including Windows Defender and SmartScreen, often trust signed executables more than unsigned ones, reducing warnings for users.
However, attackers abuse this trust by:
Signing malware to make it appear legitimate.
Bypassing security filters that would otherwise block unsigned or suspicious files.
Evading detection by mimicking trusted software.
Extended Validation (EV) certificates were once the gold standard, requiring strict business verification. But due to their high cost and difficulty in obtaining, cybercriminals are now turning to Microsoft’s Trusted Signing as an easier alternative.
Why Cybercriminals Target Extended Validation (EV) Certificates

EV certificates provide the highest level of trust, often granting an immediate SmartScreen reputation boost. However, attackers face challenges:
Strict verification (requires proof of business legitimacy).
High costs (must register fake companies or steal existing certificates).
Quick revocation once abuse is detected.
Due to these hurdles, cybercriminals are shifting to Microsoft’s Trusted Signing, which offers a faster, cheaper, and more disposable way to sign malware.
How Microsoft’s Trusted Signing Service Is Being Abused
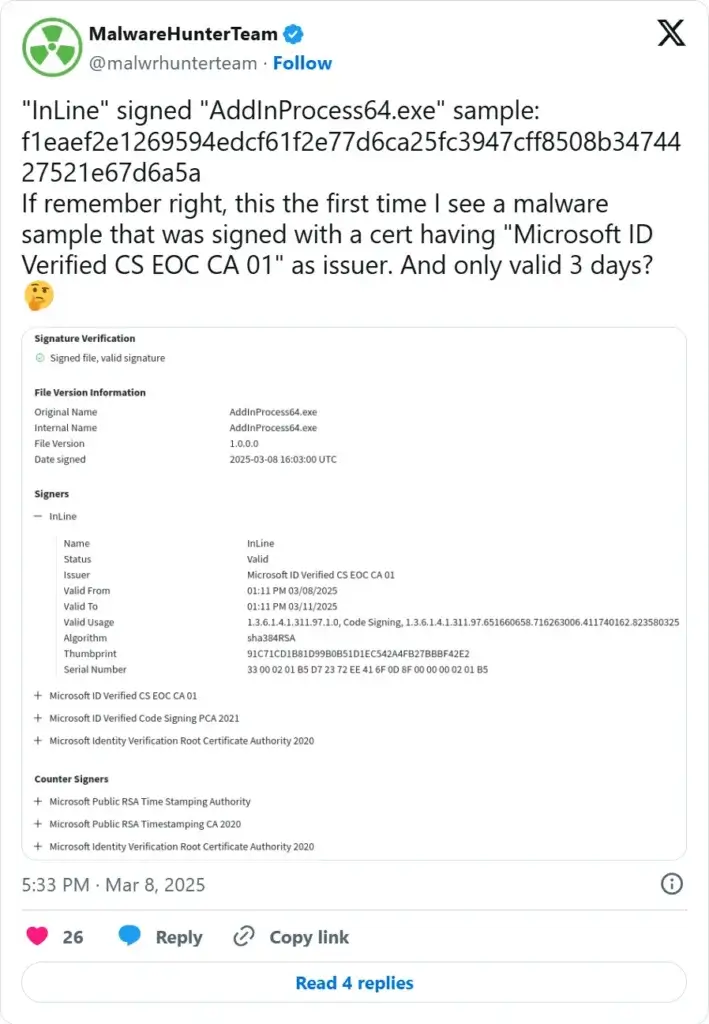
-Malware hunter Team’s Tweet on X
Microsoft’s Trusted Signing allows developers to sign software without directly managing certificates. Unfortunately, attackers exploit key weaknesses:
Short-lived three-day certificates that remain valid until revoked.
Easier verification compared to EV certificates.
SmartScreen trust boost, making malware appear safe.
Cybercriminals create fake developer accounts, sign malware, and distribute it before Microsoft detects and revokes the certificate.
Real-World Malware Campaigns Using Microsoft’s Trusted Signing
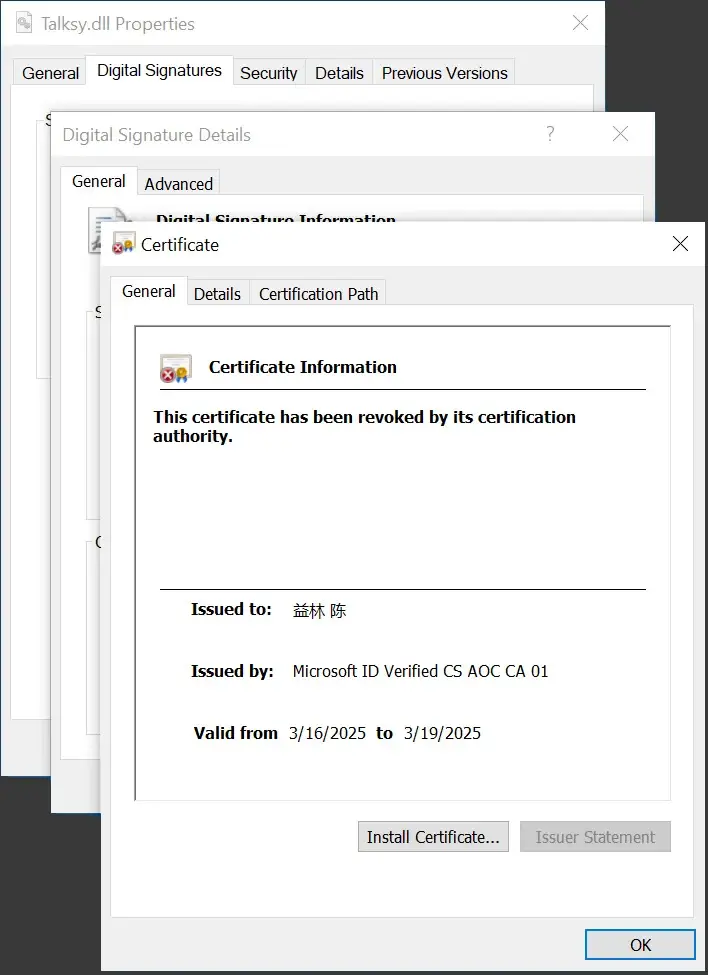
-signed-dll-from-crazy-evil-traffers-campaign
Source: BleepingComputer
Several high-profile malware families have abused this service:
Crazy Evil Traffers Crypto-Theft Campaign – Used signed malware to steal cryptocurrency.
Lumma Stealer – A credential-stealing malware signed via Trusted Signing.
These campaigns leverage Microsoft ID Verified CS EOC CA 01 certificates, allowing them to bypass traditional security checks.
Why Attackers Are Switching from EV Certificates to Microsoft’s Trusted Signing
Recent changes in EV certificate requirements have made them harder to obtain, while Microsoft’s service offers:
Faster approval (less stringent checks).
Lower costs (no need for fake business setups).
Short-term usability (attackers only need a few days before revocation).
This shift highlights cybercriminals’ preference for quick, disposable certificates over long-term investments in stolen or fake EV certs.
Microsoft’s Response to Code-Signing Abuse
Microsoft has taken steps to combat abuse:
Revoking malicious certificates and suspending offending accounts.
Enhancing threat intelligence to detect misuse faster.
Blocking known malicious files via Defender and SmartScreen.
However, limitations remain:
Attackers can quickly register new accounts.
Malware signed before revocation remains valid until the certificate expires.
Mitigation Strategies for Organizations
To defend against signed malware, organizations should:
- Use behavioral-based detection (don’t rely solely on signatures).
- Monitor certificate transparency logs for suspicious activity.
- Implement multi-layered security (EDR, sandboxing, network filtering).
Stay updated on threat intelligence regarding new signing abuses.
Future improvements in code-signing security are needed to prevent further exploitation.
Conclusion
Cybercriminals are increasingly abusing Microsoft’s Trusted Signing service to sign malware, bypassing security checks that would normally flag unsigned executables. While Microsoft actively revokes malicious certificates, attackers continue exploiting the system’s speed and convenience.
Organizations must adopt advanced detection methods and stay vigilant against these evolving threats. As code-signing remains a critical security feature, both vendors and defenders must work together to close these loopholes.
Stay secure—don’t let a trusted signature fool you.
References
Why Businesses Trust SecureMyOrg for Comprehensive Network Security
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!







Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.