In this blog we will see a step-by-step guide of what goes behind a successful pentest. This not only includes the technical aspects but also the business and legal aspects of it.
If you’re tasked with the responsibility for getting your organisation’s app or website’s pentest done, this blog would definitely help you navigate the waters easily.
Table of Contents
What is a Pentest ?

Pentest also known as Pentesting, a term used interchangeably with Vulnerability Assessment and Penetration Testing ( VAPT ).
A penetration test, colloquially known as a pentest or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; this is not to be confused with a vulnerability assessment.
– Wikipedia
So essentially it’s cracking into computer systems to which you’ve the permissions to do so. If you’re familiar with bug bounty, then you might ask, then what’s the difference between bug bounty and pentest ?
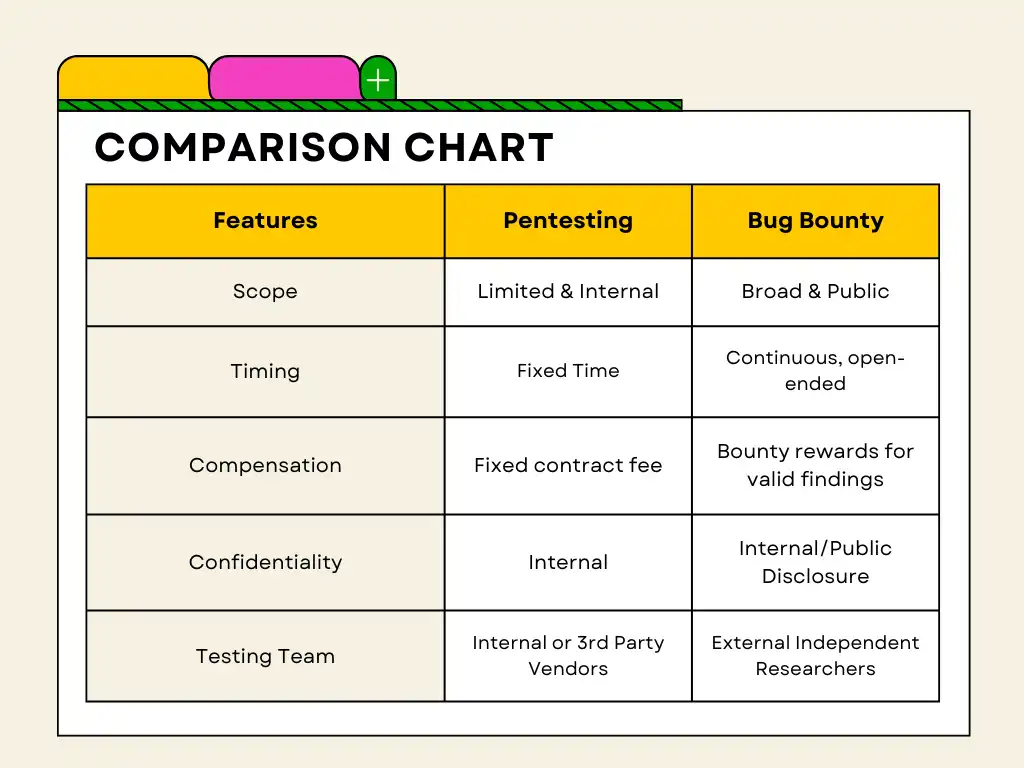
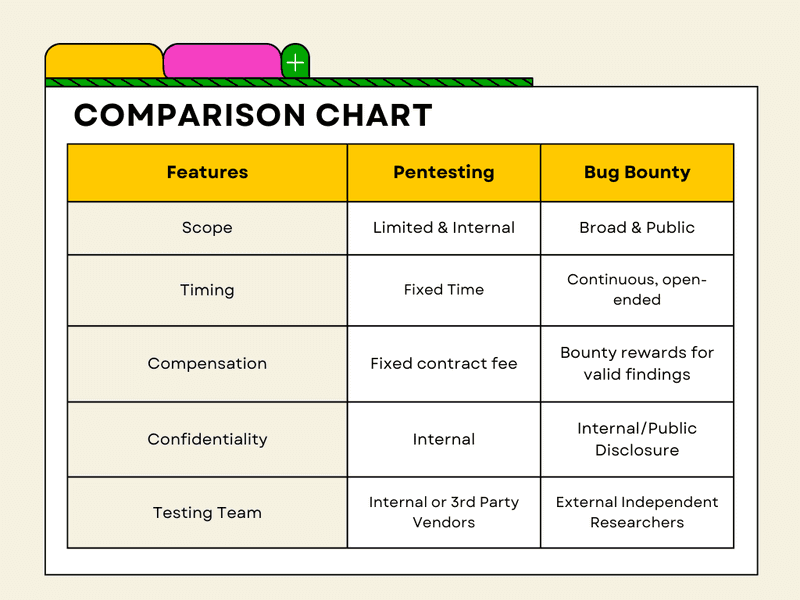
Bug Bounty vs Pentest
Bug Bounty is when organisations have put in a reward aka ‘bounty’ for finding bugs onto one of their systems aka ‘assets’, could be web application, application executable etc. In this case the organisations lay down a set of rules for anyone testing their assets and the corresponding payout ranges for the same. This usually runs for long period of time.
Why do we need a Pentest ?
- Identify Vulnerabilities: Pentests help uncover weaknesses in your systems, applications, and networks that could be exploited by attackers.
- Risk Mitigation: By identifying vulnerabilities early, you can proactively address them, reducing the risk of security breaches and their associated impacts.
- Compliance Requirements: Many industries have regulatory requirements mandating regular security testing, including Pentests, to ensure data protection and compliance.
- Protect customer’s data: Pentests are also done to avoid risking customer’s data to a breach. Pentests help identify security loopholes that can be identified by the attackers to leak sensitive customer data.
- Protect Reputation: Detecting and fixing vulnerabilities before they are exploited helps maintain customer trust and protects your organization’s reputation.
- Continuous Improvement: Pentests provide valuable insights into your security posture, enabling you to continually improve your defenses and stay ahead of emerging threats.
Steps of a Pentest
From the discovery call to the final report submission post retest, there are multiple steps involved, that we take while doing a pentest. These steps ensure a good experience for our clients and increased faith in our testing methodologies. Lets see the steps involved in a pentest ―
- Discovery Call
- Complete Formalities
- Technical Setup
- Day 0
- Daily Updates
- Preliminary Report Submission
- Retest
- Final Report Submission
Deep Dive into the Pentest Process
Let’s elaborate a bit on each of these steps.
- Discovery Call
This is the first call that we have with the client. You can book this here.
This call helps us do requirement gathering, what are the targets, scope, guidelines we should be aware of, assets that need to be tested more rigorously etc. We record all of this and more from the client in our VAPT Intake Questionnaire.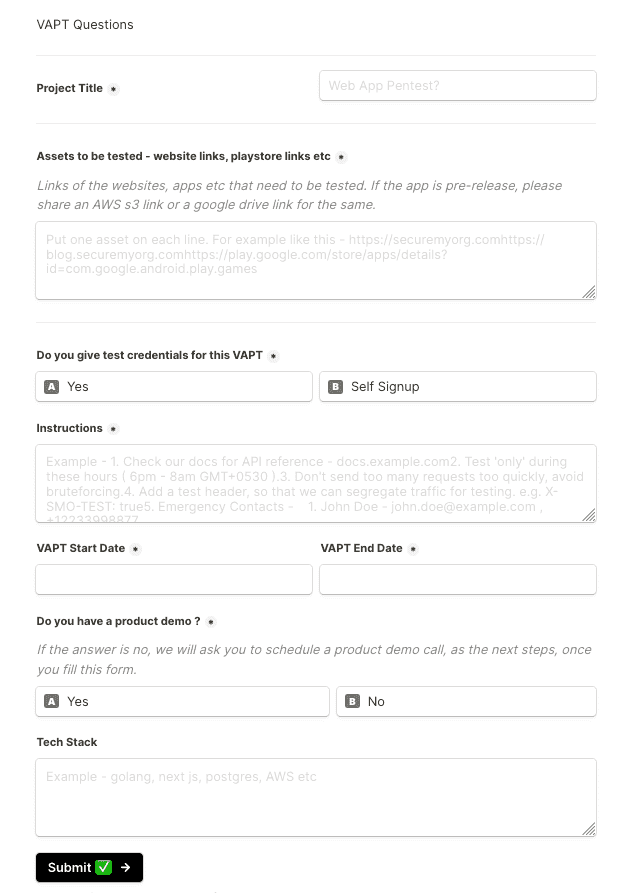
- Complete Formalities
Once the client submits the requirements, comes the part where you need to formalise the pentest and make it legally binding. To share any more information an Non Disclosure Agreement ( NDA ) is required. Either we share the NDA or the client shares across and we e-sign it. Post this we create a Statement of Work ( SoW ) and share a proposal which includes the SoW and quote for the work. - Technical Setup
Once the legalities have completed, we move forward with the technical setup. This includes setting timelines, adding the Point of Contact ( PoC ) from the client to a pentest specific slack channel and getting our VPN IP whitelisted. The slack channel serves as a faster way of communication between the client and our team, which includes the pentesters and a dedicated pentest manager. We ask the client to whitelist our VPN IP so that they can easily filter out our traffic and we can be sure that we aren’t getting ratelimited for our testing. - Day 0
Now that everything is set up. We kick-off the pentest. We call this the Day 0. - Daily Updates
We submit a daily summary of the pentest in our slack channel to keep the client in the loop. It’s usually the summary of endpoints tested and for what kind of vulnerabilities. This also serves as a touchbase point for the client to know what we have already covered during our pentest.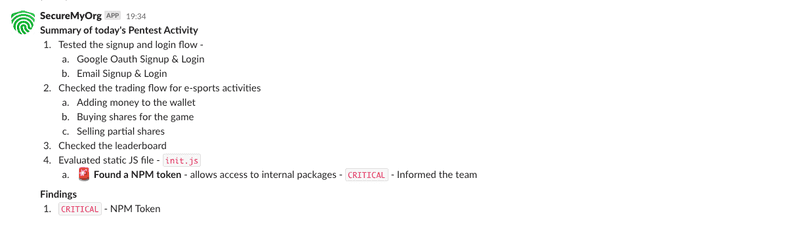
- Preliminary Report Submission
On the pentest due date, we submit a preliminary report and setup a discussion call to go over all the findings. The report has all the findings, steps to reproduce and proof-of-concepts attached to it. If the client has asked us for nuclei templates, we provide them during this phase. This helps them to self test their fixes before finally asking us to retest it. - Retest
Once the client has fixed the findings, we do a retest. We check the working steps and then also try to find bypasses to the client’s fixes. This usually takes 1-2 days. If there are any bypasses, we inform the client of the same and ask them to fix those. Once, those are fixed we retest the bypasses. Once all the findings have been fixed, we gear up for the final report submission. - Final Report Submission
The final report is a password protected PDF, that contains theupdated statusof the findings. Alongwith this we offer our clients a ‘Certificate of Attestaion‘, mentioning the pentest summary and date.
Considerations to bear in mind when undergoing a pentest for your organization
- Know your Pentesters – This should be done in the
Discovery Call. Have a chat with them and talk with them about their methodology and their expertise in testing applications from different types of industries such as fintech, edtech etc. - Inform Internally – Before starting the pentest, make sure to keep the infra team and the backend team in the loop. This helps in avoiding unnecessary surprises and promotes smooth and timely testing.
- The Point of Contact – Should be someone who’s more security initiated, ideally a security engineer.
- Staging Environment – Pentesting should be done on a close replica of your prod environment and not on the prod environment. Many times companies dont have parity between staging and production environment, hence they conduct vapt on prod. This should be avoided.
- Identifying Testing Traffic – Ask the agency to add a unique header in all the requests they’re sending to your machines. This helps in avoiding unnecessary alert fatigue, as those testing payloads might trigger a lot of internal systems and alarms.
- What’s Left Out – Not only ask for what’s tested for but also make sure to get updated with whatever is left out and why.
- Video Proof of Concept – Prefer video proof of concepts for easy replication.
- Preliminary Report Submission – Post the preliminary report submission, make sure to apprise the DevOps and backend team.
Important things in a Pentest
Setting Clear Expectations
Make sure to properly document your expectations in the SoW.Clear and Prompt Communication
Keep your client updated of your work. They shouldn’t feel that you aren’t working on the pentest.- Apprise them of any critical findings, ASAP.
- Let them know, if you’ll be load testing their systems.
Accountability
We maintain this by submitting a daily report of endpoints tested and test cases on our slack channel.
In the end of the pentest, we also submit the full log of our BURP endpoints tested and coverage to ensure accountability and transparency.Timeliness
Make sure to give the deliverables on time. There could be exploits that would be taking much time to exploit, in cases where there’s a delay inform the client accordingly.
Relevant Posts

Mastering Burp Suite: The Ultimate Guide -SecureMyOrg
Burp Suite is a cybersecurity powerhouse, offering tools like an intercepting proxy, vulnerability scanner, and repeater to identify and exploit web application vulnerabilities effectively.
Metasploit for Penetration Testing: Installation and Usage
Metasploit is a powerful penetration testing framework that allows security professionals to identify and exploit vulnerabilities in systems. In this blog, we’ll guide you through the installation process and provide tips on how to effectively use Metasploit for your security assessments. Whether you’re a beginner or an experienced user, you’ll find valuable insights to enhance your penetration testing skills.

Best Network Penetration Testing Tools in 2024
Network penetration testing tools are the cornerstone of modern cybersecurity, we look into the best network penetration testing tools in
2024

Network Penetration Testing 2: Why it is Important to Modern Businesses -SecureMyOrg
Network penetration testing is not just a technical exercise; it’s a strategic investment in the security and resilience of your organization. Here’s why it is important to modern businesses.

Command Injection Vulnerability in D-Link NAS Devices: Recommended Fixes -SecureMyOrg
A critical command injection vulnerability (CVE-2024-10914) in D-Link NAS devices exposes thousands of internet-connected units to potential exploitation. we look into the technical aspect of this, and some possible fixes

Network Penetration Testing: Boosting Your Security Strategy -SecureMyOrg
From safeguarding data to meeting compliance standards, network penetration testing is the cornerstone of a robust cybersecurity strategy.