Cybersecurity threats continue to evolve, with attackers employing increasingly sophisticated methods to exploit vulnerabilities. In this environment, network penetration testing stands as a critical practice to identify, address, and prevent security weaknesses. In Part 2 of this comprehensive guide, we’ll explore why network penetration testing is indispensable for modern businesses, its benefits, and how it serves as a proactive defense mechanism in the face of cyber risks.
Table of Contents
Understanding Network Penetration Testing

Network penetration testing is a simulated cyberattack performed by ethical hackers to evaluate the security of an organization’s IT infrastructure. It identifies vulnerabilities in systems, devices, firewalls, and network protocols that malicious actors could exploit. Pen testing doesn’t just highlight weaknesses; it also provides actionable insights to mitigate risks and fortify defenses.
By replicating real-world attack scenarios, network penetration testing enables organizations to stay ahead of potential threats and reduce the risk of data breaches, financial loss, and reputational damage.
Why is Network Penetration Testing Important to Businesses?
With the rise of digital transformation, businesses now depend on interconnected systems for critical operations, ranging from supply chain management to customer relationship management (CRM). While this connectivity drives innovation, it also introduces vulnerabilities that cybercriminals exploit.
- Increasing Frequency of Cyberattacks: A 2023 report by Cybersecurity Ventures predicts that cybercrime will cost the global economy $10.5 trillion annually by 2025. Small businesses, which often lack robust defenses, are especially vulnerable.
If it were measured as a country, then cybercrime — which is predicted to inflict damages totaling $6 trillion USD globally in 2021 — would be the world’s third-largest economy after the U.S. and China.
–from Special Report: Cyberwarfare In The C-Suite. - Regulatory Compliance: Businesses must adhere to data protection standards like GDPR, HIPAA, and PCI DSS. Non-compliance can result in hefty fines and legal challenges.
- Reputation Management: A single breach can erode customer trust, causing long-term damage to a company’s brand.
Network penetration testing is essential to mitigate these risks, ensuring businesses remain compliant and maintain customer confidence.
Benefits of Network Penetration Testing
Proactive Vulnerability Identification
Pen testing allows businesses to uncover vulnerabilities before malicious actors exploit them. This proactive approach minimizes potential attack surfaces, ensuring that weaknesses are addressed promptly.Regulatory Compliance and Risk Management
Many industries require regular penetration testing as part of their compliance mandates. By performing pen tests, businesses can demonstrate their commitment to cybersecurity and avoid penalties for non-compliance.Enhanced Incident Response
Penetration testing equips IT teams with insights into how attackers might infiltrate the network, enabling them to improve incident response plans. This reduces downtime and mitigates damage during real-world cyber incidents.Cost Savings
The cost of mitigating a cyberattack often far exceeds the investment in penetration testing. By identifying and addressing vulnerabilities early, businesses can avoid the financial and operational repercussions of a breach.Building Stakeholder Confidence
Demonstrating robust cybersecurity measures reassures clients, investors, and partners that the business takes data protection seriously.
Industries That Benefit Most from Penetration Testing
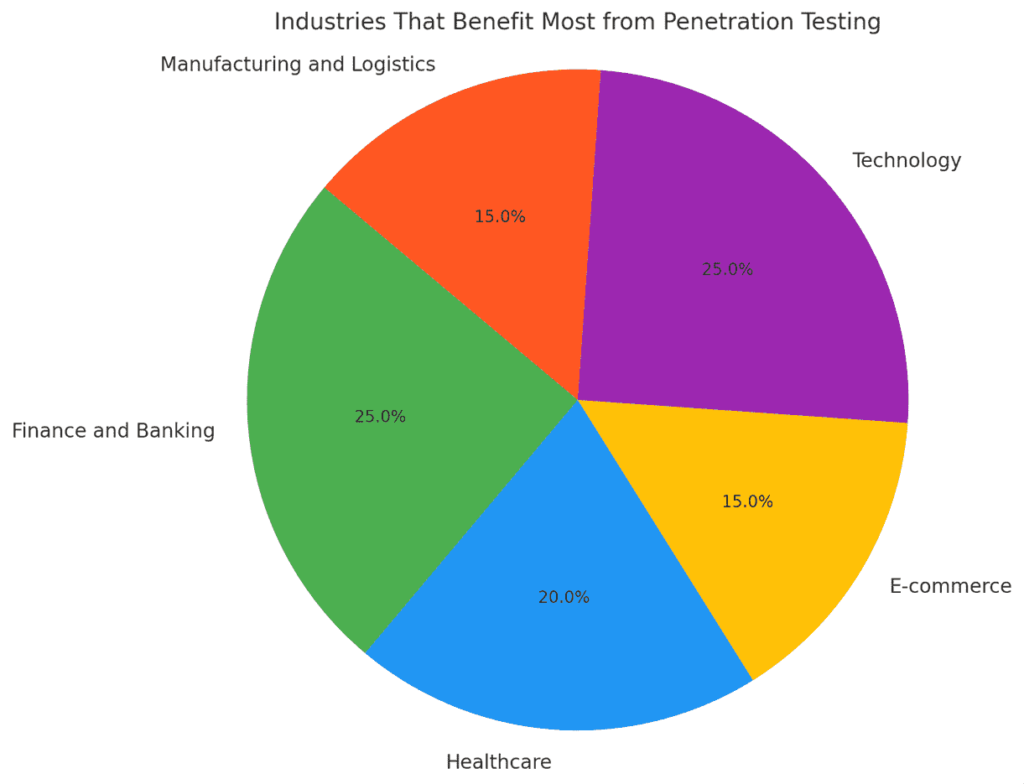
While all businesses can benefit from penetration testing, certain industries are particularly reliant on this practice:
Finance and Banking
Financial institutions handle vast amounts of sensitive data, making them prime targets for cyberattacks. Pen testing helps identify vulnerabilities in systems like ATMs, online banking portals, and mobile apps.Healthcare
Healthcare providers must protect patient records under regulations like HIPAA. Pen testing ensures compliance while safeguarding against ransomware and data breaches.E-commerce
Online retailers process financial transactions and customer information, making cybersecurity a top priority. Penetration testing mitigates risks like credit card fraud and website defacement.Technology
Tech companies rely on interconnected networks to deliver services. Regular testing helps secure APIs, cloud environments, and IoT devices.Manufacturing and Logistics
The rise of smart factories and supply chain digitization has increased exposure to cyber risks. Pen testing protects against disruptions caused by attacks on industrial control systems.
Why Businesses Trust SecureMyOrg for Comprehensive Network Security
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!







Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.

Conclusion: Secure Your Business with Penetration Testing
In an age where cyber threats are omnipresent, network penetration testing is not a luxury but a necessity for modern businesses. By proactively identifying vulnerabilities, ensuring compliance, and fostering customer trust, it empowers organizations to build resilient IT infrastructures.
Whether you’re a small business or a global enterprise, prioritizing penetration testing is the key to staying ahead of cyber adversaries. Take the next step in securing your digital assets—partner with a trusted cybersecurity firm like SecureMyOrg to schedule your network penetration testing today.
Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.
