Nessus, a powerful vulnerability scanning tool, is widely used by IT professionals and ethical hackers to discover weaknesses in network systems. In this blog, we’ll provide a step-by-step guide on how to perform a network vulnerability scan with Nessus, from setup to report analysis.
Table of Contents
What Is Nessus?

Nessus, developed by Tenable, is a vulnerability scanning tool designed to help organizations identify and fix vulnerabilities across their IT infrastructure. It offers comprehensive scanning capabilities for network devices, servers, and applications, making it a staple in the toolkit of security professionals.
Why Use Nessus for Network Vulnerability Scanning?
Nessus is a leading tool in the cybersecurity industry for several compelling reasons:
Comprehensive Scanning: Nessus detects a wide range of vulnerabilities, including misconfigurations, outdated software, missing patches, and security flaws in network devices, servers, and applications. Its extensive plugin library ensures it stays up-to-date with the latest threats.
Ease of Use: With its intuitive interface and guided setup process, Nessus is user-friendly even for those new to vulnerability management. The streamlined workflows allow users to quickly configure and launch scans.
Customizability: Nessus supports tailored scan policies, allowing organizations to focus on specific areas of concern, such as compliance standards or critical infrastructure.
Cost-Effective: Offering both free and professional versions, Nessus provides robust features at an accessible price point, making it suitable for organizations of all sizes.
Detailed Reporting: Nessus generates actionable insights with detailed scan reports, categorized by severity levels. This allows IT teams to prioritize and address vulnerabilities efficiently.
Support for Compliance: Nessus helps organizations meet industry regulations and standards, such as PCI DSS, HIPAA, and ISO 27001, by identifying compliance gaps and suggesting fixes.
Proven Track Record: Trusted by security professionals worldwide, Nessus has a long history of reliable performance and continuous improvements to meet evolving security needs.
Preparing for a Network Vulnerability Scan
Before initiating a scan, ensure the following prerequisites are in place:
Install Nessus: Download Nessus from the official website and follow the installation instructions for your operating system.
Configure Nessus: Once installed, access the Nessus web interface, create an account, and activate it with the appropriate license key.
Identify the Scope: Define the network range, IP addresses, or specific devices you want to scan.
Obtain Permissions: Ensure you have authorization to perform vulnerability scans, especially in enterprise environments.
Update Plugins: Regularly update Nessus plugins to ensure the tool can detect the latest vulnerabilities.
Step-by-Step Guide to Perform a Network Vulnerability Scan
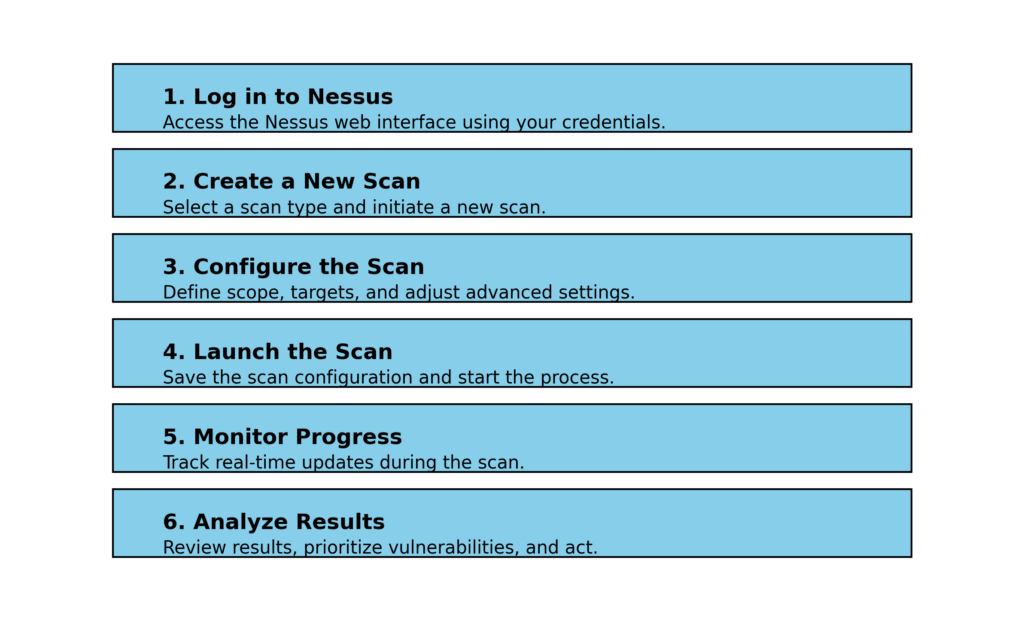
Step 1: Log in to Nessus
Access the Nessus web interface using your browser and log in with your credentials.
Step 2: Create a New Scan
Navigate to the Scans tab and click on New Scan.
Select the scan type. For network vulnerability scanning, choose Basic Network Scan or a custom template that suits your requirements.
Step 3: Configure the Scan
Name the Scan: Provide a descriptive name, such as “Weekly Network Scan.”
Target the Scope: Enter the IP addresses or range of the devices to be scanned.
Adjust Settings: Configure advanced settings, such as scan schedules, port ranges, or exclusions, to optimize the process.
Step 4: Launch the Scan
Click on Save to store the scan configuration.
Select the scan from the list and click Start to initiate the scan.
Step 5: Monitor Progress
As the scan progresses, Nessus will display real-time updates. Larger networks may take longer to scan, depending on the scope and configurations.
Step 6: Analyze the Results
Once the scan is complete, open the scan report.
Review the identified vulnerabilities, categorized by severity (Critical, High, Medium, Low, and Informational).
Use the provided details, including CVE IDs, descriptions, and remediation steps, to address each vulnerability.

Best Practices for Network Vulnerability Scanning with Nessus
Schedule Regular Scans: Set up recurring scans to ensure continuous monitoring and vulnerability management.
Prioritize High-Severity Issues: Address critical vulnerabilities first to minimize risk.
Limit Scan Impact: Avoid running scans during peak hours to prevent disruptions.
Use Authentication: Enable authenticated scanning for more accurate results.
Export Reports: Share detailed reports with stakeholders to ensure accountability and follow-up actions.
Conclusion
Nessus is a versatile and powerful tool that simplifies the process of identifying and addressing network vulnerabilities. By following the steps outlined above, you can effectively use Nessus to safeguard your IT infrastructure against potential threats. Remember, vulnerability management is an ongoing process that requires regular scanning, monitoring, and remediation.
Investing in tools like Nessus and adhering to best practices ensures your network remains resilient against evolving cyber threats. Start your journey toward enhanced network security today by leveraging the power of Nessus.
Why Businesses Trust SecureMyOrg for Comprehensive Network Security
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!






Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
