The rapid adoption of Internet of Things (IoT) devices has transformed the way we live, offering convenience, automation, and enhanced connectivity. From smart homes and industrial automation to healthcare and transportation, IoT devices are becoming an integral part of modern infrastructure. However, this digital revolution has also introduced severe cybersecurity risks, with one of the most concerning being the rise of IoT botnets—massive networks of compromised smart devices exploited for cybercriminal activities.
This blog explores how IoT botnets are formed, the threats they pose, notable attacks, and strategies to mitigate these risks.
Table of Contents
What is an IoT Botnet?

An IoT botnet is a network of compromised internet-connected devices—such as routers, smart cameras, smart TVs, and industrial sensors—that are infected with malware and remotely controlled by hackers. Unlike traditional botnets that primarily target computers and servers, IoT botnets exploit security weaknesses in smart devices, which often lack proper cybersecurity protections.
How Do IoT Botnets Work?
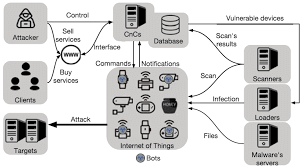
Overview of an IoT Botnet -Research Gate
IoT botnets follow a systematic attack cycle:
Infection – Hackers exploit weak passwords, unpatched vulnerabilities, or unsecured communication protocols to inject malware into IoT devices.
Propagation – Once infected, devices attempt to spread the malware to other vulnerable IoT systems.
Command and Control (C2) – The compromised devices connect to a C2 server, allowing attackers to issue commands remotely.
Execution of Cyber Attacks – The infected devices are then used to launch attacks such as Distributed Denial-of-Service (DDoS), credential theft, spam distribution, cryptojacking, and data exfiltration.
Why Are IoT Devices Prime Targets for Botnets?
IoT devices are highly susceptible to botnet infections due to several factors:
1. Weak Security Configurations
Many IoT devices come with default usernames and passwords, which users fail to change, making them easy targets for brute-force attacks.
Some manufacturers hard-code credentials into firmware, leaving no way to secure the device.
2. Lack of Regular Updates
Unlike computers and smartphones, IoT devices rarely receive security updates, leaving them vulnerable to known exploits.
3. Always-Connected Nature
IoT devices are always online, providing continuous access for attackers to exploit and control them remotely.
4. Sheer Volume of IoT Devices
The number of IoT devices is rapidly growing, with projections estimating over 29 billion devices worldwide by 2030. This scale provides cybercriminals with an extensive attack surface.
5. Limited Security Awareness
Many IoT device owners are unaware of cybersecurity risks, making them unlikely to implement basic protection measures.
Notable IoT Botnet Attacks
1. The Mirai Botnet (2016)
One of the most infamous IoT botnets, Mirai, infected thousands of IoT devices, including DVRs, security cameras, and routers. The botnet was used to launch massive DDoS attacks, disrupting major websites such as Twitter, Netflix, and Reddit.
How it worked: Mirai scanned the internet for IoT devices with default credentials, infecting them with malware and turning them into bots.
Impact: Peak attack reached 1.2 Tbps, making it one of the largest DDoS attacks in history.
2. The Mozi Botnet (2019-Present)
Mozi is a peer-to-peer (P2P) IoT botnet that spreads through weak Telnet passwords and unpatched vulnerabilities.
Unique feature: Uses blockchain-based C2 mechanisms, making it more resilient against takedowns.
Impact: Has infected millions of IoT devices globally, launching DDoS attacks and data theft campaigns.
3. The Hakai Botnet (2018)
This botnet specifically targeted Huawei and Realtek routers, exploiting unpatched vulnerabilities.
Impact: Disrupted global networks through DDoS attacks.
Key vulnerability: Relied on outdated firmware with weak security patches.
4. The VPNFilter Botnet (2018)
VPNFilter infected over 500,000 routers worldwide, capable of spying on internet traffic and delivering destructive payloads.
Impact: Could execute man-in-the-middle attacks, modify web traffic, and steal sensitive credentials.
Cyber Threats Enabled by IoT Botnets
1. Distributed Denial-of-Service (DDoS) Attacks
IoT botnets are widely used to flood targeted servers with traffic, overwhelming them and causing service disruptions.
Example: Mirai botnet’s attack on Dyn, which affected major websites globally.
2. Data Theft and Espionage
IoT devices collect vast amounts of sensitive data, making them prime targets for cyber espionage.
Example: Compromised smart home devices could be used for eavesdropping or data collection.
3. Cryptojacking (Unauthorized Crypto Mining)
IoT botnets can hijack devices to mine cryptocurrency, consuming bandwidth and processing power.
Example: Smominru botnet infected over 500,000 devices to mine Monero cryptocurrency.
4. Spam and Phishing Campaigns
IoT botnets distribute massive volumes of spam emails containing malware or phishing links.
Example: Cutwail botnet, responsible for sending millions of spam emails per hour.
5. Ransomware Distribution
IoT botnets can be leveraged to spread ransomware infections, locking users out of their devices.
Example: Ryuk ransomware, which has been linked to botnet-driven attacks.
How to Protect IoT Devices from Botnets
Given the growing risks posed by IoT botnets, organizations and individuals must take proactive measures to secure their devices:
1. Change Default Credentials
-
Immediately update factory-set usernames and passwords on all IoT devices.
-
Use strong, unique passwords and enable multi-factor authentication (MFA) where possible.
2. Regularly Update Firmware and Software
-
Install security patches and updates to fix known vulnerabilities.
-
If a device is no longer supported with updates, consider replacing it with a secure alternative.
3. Segment IoT Networks
-
Separate IoT devices from critical network infrastructure using VLANs or firewall rules.
-
Restrict IoT devices from communicating with external networks unnecessarily.
4. Disable Unnecessary Services and Ports
-
Turn off features like Telnet, SSH, or UPnP if they are not in use.
-
Close unused open ports that could be exploited.
5. Monitor Network Traffic
-
Use Intrusion Detection and Prevention Systems (IDPS) to identify and block suspicious IoT activity.
-
Deploy AI-based anomaly detection to spot abnormal network behavior.
6. Implement Zero Trust Security
-
Restrict device access based on security policies.
-
Use identity verification and continuous monitoring for connected IoT devices.
Conclusion
The weaponization of IoT devices through botnets represents a growing cybersecurity crisis. With billions of IoT devices coming online, the attack surface for cybercriminals continues to expand. Proactive security measures, improved awareness, and regulatory policies are crucial in mitigating IoT botnet threats.
By understanding how these botnets operate and implementing robust security strategies, businesses and individuals can safeguard their networks against evolving cyber threats.
References
Why Businesses Trust SecureMyOrg For Comprehensive Network Security
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!







Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.
