Botnets are among the most dangerous and widespread cyber threats in the modern digital landscape. They consist of a network of compromised devices—computers, servers, IoT devices, and more—controlled remotely by cybercriminals. These networks are used for malicious activities such as Distributed Denial-of-Service (DDoS) attacks, data theft, phishing scams, and ransomware distribution.
This article explores what a botnet is, how cybercriminals control infected devices, and the risks they pose to businesses and individuals. We will also discuss how to detect and protect against botnet infections.
Table of Contents
What is a Botnet?
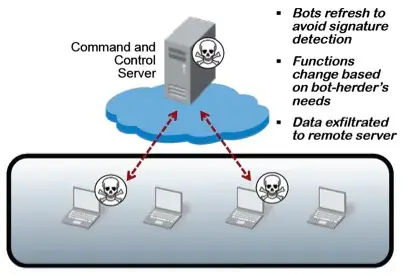
A botnet (short for “robot network”) is a group of internet-connected devices infected with malware and controlled by a single entity, known as the bot herder or botmaster. These infected devices, called bots or zombies, follow commands from the attacker, often without the user’s knowledge.
Botnets can range from a few thousand devices to millions, giving hackers massive power to launch coordinated cyber attacks. Cybercriminals use botnets for various purposes, from flooding websites with traffic (DDoS attacks) to spreading malware and stealing sensitive information.
How Are Botnets Created?
Botnets are formed when hackers infect multiple devices using malware, typically distributed through:
Phishing emails with malicious attachments or links.
Drive-by downloads from compromised or malicious websites.
Exploiting software vulnerabilities in outdated systems.
Infected USB drives or removable media.
IoT device vulnerabilities, such as weak passwords on smart home gadgets.
Once a device is infected, it secretly connects to the botnet’s command and control (C2) server, allowing hackers to issue remote commands.
How Cybercriminals Control Botnets
Botmasters use various command-and-control (C2) techniques to manage botnets. These include:
1. Centralized (Client-Server) Botnets
In a centralized botnet, all infected devices communicate with a single command-and-control (C2) server controlled by the hacker. The C2 server sends instructions, and bots execute them.
Advantages for hackers: Easy to control and monitor.
Weakness: If the C2 server is detected and taken down, the entire botnet collapses.
2. Peer-to-Peer (P2P) Botnets
P2P botnets eliminate the need for a central C2 server. Instead, bots communicate with each other, spreading commands in a decentralized manner.
Advantages for hackers: Harder to shut down since no single server controls it.
Weakness: More complex to manage compared to centralized botnets.
3. Domain Generation Algorithm (DGA) Botnets
DGA botnets generate random domain names that infected bots connect to for instructions. If security teams block one domain, the botnet simply moves to a newly generated domain.
Advantages for hackers: More resilient against detection and takedowns.
Weakness: Requires continuous domain name registrations, which can be tracked.
Common Uses of Botnets in Cybercrime
1. Distributed Denial-of-Service (DDoS) Attacks
DDoS attacks overwhelm websites or servers with traffic, causing downtime and service disruptions. Cybercriminals rent out botnets to launch massive DDoS attacks against businesses, governments, and competitors.
2. Phishing and Spam Campaigns
Botnets are used to send millions of spam emails containing phishing links or malware attachments. These emails trick users into revealing sensitive information or downloading malicious software.
3. Data Theft and Credential Harvesting
Some botnets are designed to steal passwords, banking credentials, and personal information by logging keystrokes or intercepting communications.
4. Cryptojacking (Illegal Crypto Mining)
Cybercriminals use botnets to hijack device resources and mine cryptocurrencies like Bitcoin or Monero without the owner’s consent. This can slow down affected systems and increase electricity usage.
5. Ransomware Distribution
Botnets help spread ransomware by infecting multiple devices at once. The malware encrypts data, and attackers demand payment to restore access.
Examples of Notorious Botnets
1. Mirai Botnet
One of the most infamous botnets, Mirai infected IoT devices such as routers and cameras by exploiting weak passwords. It launched massive DDoS attacks, including the 2016 attack on Dyn, which temporarily took down Amazon, Twitter, and Netflix.
2. Zeus Botnet
A banking malware botnet that stole financial credentials by logging keystrokes. Zeus infected millions of computers worldwide, leading to significant financial losses.
3. Emotet Botnet
Originally a banking trojan, Emotet evolved into a malware delivery botnet, distributing ransomware and spyware via phishing campaigns.
4. TrickBot Botnet
A sophisticated botnet used for stealing sensitive data, distributing ransomware, and infecting large networks, including government agencies.
How to Detect and Prevent Botnet Infections
Signs Your Device Might Be Part of a Botnet
Unusual network activity – Unexpected spikes in data usage or outgoing traffic.
Slow performance – Devices running slower due to background botnet activity.
Frequent crashes or freezes – Malware-related instability in the system.
Strange emails sent from your account – Bots may use your email to send spam.
High CPU usage – Cryptojacking botnets use device resources for mining.
How to Protect Against Botnet Infections
Keep Software and Devices Updated
Regularly update operating systems, applications, and firmware to patch security vulnerabilities.
Use Strong, Unique Passwords
Avoid default passwords on IoT devices and enable multi-factor authentication (MFA).
Install Antivirus and Anti-Malware Software
Use reputable security solutions to detect and remove malware infections.
Be Cautious of Phishing Emails and Suspicious Links
Never click on unknown links or download attachments from unverified sources.
Monitor Network Traffic
Use firewalls and network monitoring tools to detect unusual activities.
Disable Unused Services and Ports
Reduce the attack surface by turning off unnecessary features on devices.
Enable IoT Security Measures
Secure smart devices by changing default settings and using secure connections.
Regularly Scan for Malware
Run periodic security scans to identify and remove potential threats.
Conclusion
Botnets are a major cyber threat, capable of launching large-scale attacks, stealing sensitive data, and disrupting critical services. Cybercriminals use command-and-control networks to operate botnets, leveraging infected devices for malicious purposes.
Understanding how botnets work, how cybercriminals control them, and how to protect against them is crucial for businesses and individuals. By implementing strong security practices, staying vigilant, and using advanced cybersecurity tools, you can reduce the risk of becoming a botnet victim.
In an era of growing cyber threats, awareness and proactive defense are key to safeguarding digital assets from botnet-driven attacks.
References
Why Businesses Trust SecureMyOrg For Comprehensive Network Security
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!







Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Recent Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.
