We live in a digital age, and securing sensitive information is more critical than ever. From online banking to encrypted messaging, asymmetric encryption plays a crucial role in safeguarding data. But what exactly is asymmetric encryption, and how does it work? In this blog, we explore its principles, key components, applications, pros, cons, and its role in modern cybersecurity.
Table of Contents
Introduction to Asymmetric Encryption
Asymmetric encryption, also known as public-key cryptography, is a method of encrypting data using two mathematically linked keys: a public key and a private key. Key pairs are generated with cryptographic algorithms based on mathematical problems that are easy to compute in one direction (one-way functions).
- Public Key: This key is shared openly and used for encrypting data or verifying digital signatures.
- Private Key: This key is kept secret and used for decrypting data or creating digital signatures.
Unlike symmetric encryption, which uses the same key for both encryption and decryption, asymmetric encryption separates these processes into distinct roles. This distinction is what makes it uniquely secure and versatile.
How Does Asymmetric Encryption Work?
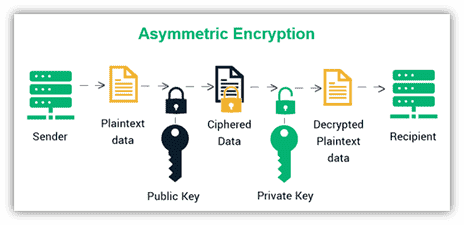
The asymmetric encryption process involves three primary steps: key generation, encryption, and decryption.
Key Generation:
- A cryptographic algorithm, such as RSA (Rivest-Shamir-Adleman) or ECC (Elliptic Curve Cryptography), generates a pair of keys.
- These keys are mathematically linked, ensuring that data encrypted with one can only be decrypted with the other.
Encryption:
- The sender uses the recipient’s public key to encrypt the data. Since the public key is widely available, anyone can encrypt a message intended for the recipient.
Decryption:
- The recipient uses their private key to decrypt the data. Without access to this private key, the encrypted data remains secure.
Some Common Asymmetric Encryption Algorithms
As said earlier, key pairs are generated with cryptographic algorithms based on one way functions. Here are some [common algorithms in asymmetric encryption]:
- RSA (Rivest-Shamir-Adleman)
- Elliptic Curve Cryptography (ECC)
- Diffie-Hellman (DH)
- ElGamal
- DSA (Digital Signature Algorithm)
- ECDSA (Elliptic Curve Digital Signature Algorithm)
- Ed25519
Use Case of Algorithms in Asymmetric Encryption: RSA
RSA (Rivest-Shamir-Adleman) is a popular asymmetric encryption algorithm which has various use cases such as, secure online transactions, digital signatures, and authentication.
The RSA algorithm uses the following formulas for encryption and decryption:
Encryption:
ciphertext = plaintext^e mod n
where e is the public exponent and n is the modulus (product of two large prime numbers, p and q).
Decryption:
plaintext = ciphertext^d mod n
where d is the private exponent and n is the modulus.
RSA Algorithm Use Case: Secure Online Transaction
Imagine a case whereby you want to send a secure online payment to an online store, let’s call the name of the store mega’s online. To ensure the transaction is secure, you decide to use an RSA asymmetric encryption.
Following the three simple phases, here’s what we have:
Step 1: Key Pair Generation
Mega’s online generates a pair of keys: a public key (e, n) and a private key (d, n). The public key is shared with you, while the private key is kept secret.
Step 2: Encryption
If you want to send a payment of $100 to Mega’s online store. You’ll encrypt the payment information using Mega’s public key (e, n).
ciphertext = encrypt(plaintext, e, n)
where plaintext is the payment information ($100) and ciphertext is the encrypted payment information.
Step 3: Decryption
Mega’s online receives the encrypted payment information and decrypts it using his private key (d, n).
plaintext = decrypt(ciphertext, d, n)
where ciphertext is the encrypted payment information and plaintext is the decrypted payment information ($100).
To get a clearer understanding of how the algorithm works let’s replace the variables with numbers:
- Let’s say Mega’s online public key is (e, n) = (3, 3233) and their private key is (d, n) = (1017, 3233).
- You want to send a $100 payment, so you encrypt the information using the shared public key:
- ciphertext = encrypt(100, 3, 3233) = 100^3 mod 3233 = 1000000 mod 3233 = 217
- Mega’s online receives the encrypted payment information and decrypts it using their private key:
- plaintext = decrypt(217, 1017, 3233) = 217^1017 mod 3233 = 100
- The decrypted payment information is $100, which is the original payment amount.
In this example, RSA asymmetric encryption ensures that the payment information is securely transmitted from your end to Mega’s online store.
Applications of Asymmetric Encryption

Asymmetric encryption is widely used in scenarios where secure communication is essential. Its applications include:
1. Secure Web Browsing (HTTPS)
- Asymmetric encryption is a core component of the SSL/TLS protocols used to secure websites.
- When you see a padlock icon in your browser, it indicates that asymmetric encryption is being used to establish a secure connection between your browser and the server.
2. Email Encryption
- Protocols like PGP (Pretty Good Privacy) and S/MIME (Secure/Multipurpose Internet Mail Extensions) use asymmetric encryption to secure email communication.
3. Digital Signatures
- Asymmetric encryption ensures the authenticity of digital documents by allowing recipients to verify that a message or file was not altered during transmission.
4. Cryptocurrencies
- Asymmetric encryption is fundamental to blockchain technologies, where private keys secure digital wallets and public keys verify transactions.
5. Secure File Transfers
- Tools like SSH (Secure Shell) use asymmetric encryption to secure remote access and data transfers.
Pros and Cons of Asymmetric Encryption
Pros:
Asymmetric encryption’s unique architecture addresses some of the most pressing challenges in data security. Below, we delve into the specific advantages that make it a game-changer in cryptography.
Enhanced Security:
- The private key never needs to be shared, reducing the risk of key compromise.
Scalability:
- In environments with multiple users, asymmetric encryption eliminates the need for distributing and managing a shared key for every pair of users.
Versatility:
- Asymmetric encryption can be used for both encrypting data and verifying identities through digital signatures.
Integration with Symmetric Encryption:
- Hybrid systems combine asymmetric encryption for key exchange with symmetric encryption for data transfer, balancing security and performance.
As with any technology, asymmetric encryption has its trade-offs. Here are the key limitations to consider when evaluating its role in a secure communication strategy.
Cons:
- Performance:
- It is computationally intensive and slower compared to symmetric encryption. This makes it less suitable for encrypting large volumes of data.
- Key Management:
- Protecting private keys is crucial. If a private key is lost or compromised, encrypted data becomes inaccessible or vulnerable.
- Complexity:
- Asymmetric encryption requires careful design to avoid vulnerabilities. This makes it complex and complexity is the worst enemy of security
- Quantum Computing Threat:
- Emerging quantum computing technology poses a potential risk to current asymmetric encryption algorithms. Post-quantum cryptography aims to address this challenge.
The Future of Asymmetric Encryption
As technology evolves, so too does asymmetric encryption. Key areas of focus include:
Post-Quantum Cryptography:
- Researchers are developing algorithms resistant to quantum computing attacks.
IoT Security:
- ECC’s efficiency makes it ideal for securing Internet of Things (IoT) devices.
Blockchain Advancements:
- Asymmetric encryption continues to underpin innovations in decentralized systems.
Hybrid Systems:
- The integration of symmetric and asymmetric encryption ensures optimized performance and security.
Conclusion
Asymmetric encryption is a cornerstone of modern cybersecurity, enabling secure communication, authentication, and data protection in an increasingly interconnected world. Its reliance on key pairs, mathematical robustness, and versatility make it indispensable for applications ranging from online banking to blockchain. While challenges such as performance and quantum threats remain, ongoing advancements in cryptography ensure that asymmetric encryption will continue to evolve and adapt to future needs.
Understanding its principles and applications is essential for anyone navigating the digital landscape. Whether you’re an IT professional, a developer, or a curious learner, mastering asymmetric encryption empowers you to appreciate the intricate mechanisms that keep our digital world secure.
About SecureMyOrg
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!
Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.
