In today’s digital landscape, cybersecurity threats lurk around every corner exploiting vulnerabilities in even the most secure systems. As technology advances, hackers adapt, making it crucial for organizations to stay one step ahead. Penetration testing, or pentesting, is a vital tool in the fight against cyber threats. In this article, we’ll delve into pentesting basics, types, and benefits, providing a comprehensive understanding of this essential security practice.

Table of Contents
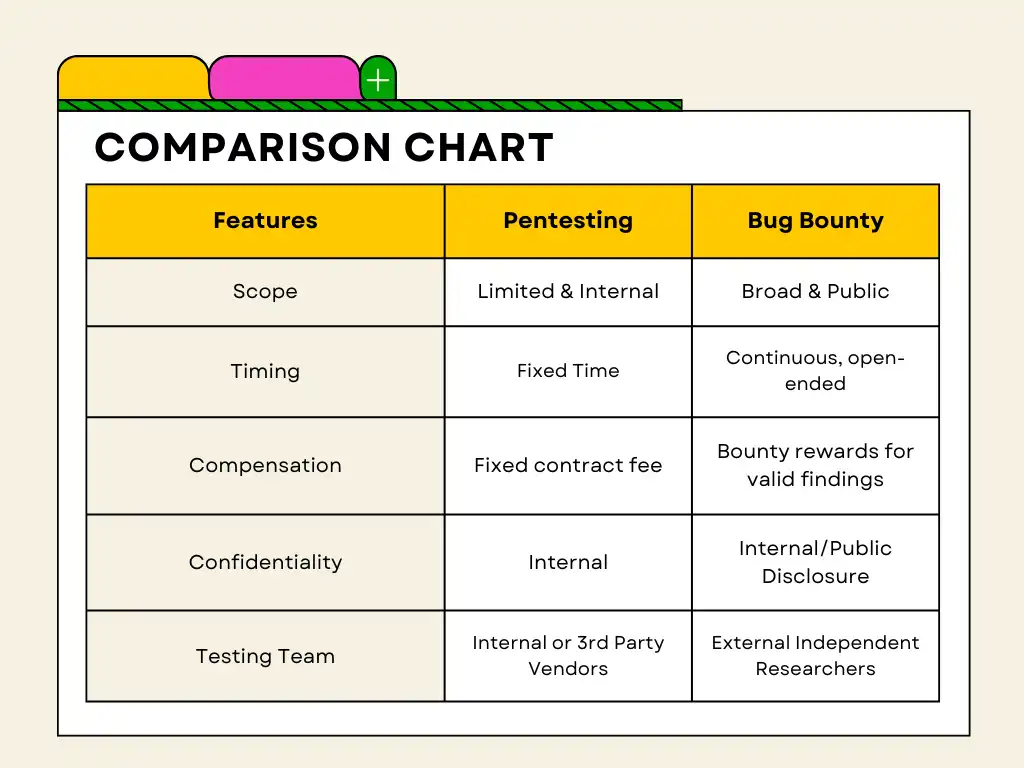
Penetration Testing is a specific type of ethical hacking that involves simulating real world attacks on a computer system, network or web application to test its defenses and identify vulnerabilities. Pentesters aim to mimic malicious hackers by using the same techniques but with permission and guidance of the organization being tested.
How is Pentesting Done?

A ‘Pentest’ is a systematic process to identify, exploit and document the vulnerabilities in the computer system of an organization. It is done in a structural approach of 5 steps or phases:
- Planning and Reconnaissance: Defining scope, gathering information, and identifying potential vulnerabilities.
- Vulnerability scanning: Using automated tools like Nmap or Nessus to scan for vulnerabilities and identify open ports, services and potential entry points.
- Exploitation and Post Exploitation: Attempting to exploit identified vulnerabilities, gaining access to systems or data, and escalating privileges.
- Reporting and Recommendations: Documenting findings, providing recommendations for remediation and mitigation, and offering guidance on security best practices.
- Remediation and Follow-up: Implementing fixes and patches, verifying effectiveness, and conducting re-testing to ensure vulnerabilities are addressed.
Types of Pentesting?
Penetration testing encompasses various types, each focusing on specific areas:
- Black Box Pentesting: Testing without prior knowledge of the system or network.
- White Box Pentesting: Testing with full knowledge of the system or network. Such as having access to the codebase from the client.
- Gray Box Pentesting: A combination of black and white box testing.
What Are Some Tools Used To Perform A Pentest?
Pentesters utilize various tools and techniques, including:
- Nmap: Network scanning and mapping.
- Metasploit: Exploitation framework.
- Burp Suite: Web application security testing.
- Wireshark: Network protocol analysis.
- Kali Linux: Comprehensive pentesting distribution
What Programming Languages are used In Pentesting?
Python is a popular and versatile language used extensively in pentesting, particularly for exploit writing, general scripting, and automation. However, there are various other languages which are used depending on the specific goals of the pentest such as; Ruby, Perl, Java, SQL, etc..
In this article, we’ll demonstrate an example of a pentest using python by scanning a network for open ports. But first, let’s cover the basics: what are ports?
What Are Ports?
In computer networking, ports are virtual endpoints that allow communication between devices. There are 65,535 ports, divided into:
- Well-known ports (0-1023): Standardized ports for common services (e.g., HTTP, FTP, SSH).
- Registered ports (1024-49151): Assigned to specific services or applications.
- Private ports (49152-65535): Available for custom use.
Port scanning involves sending network requests to a target system to identify open ports and gather information about it.
Why scan for open ports in pentesting?
It is important to scan for open ports in penetration testing in order to:
- Identify potential entry points for attackers.
- Discover vulnerable services or applications.
- Map network architecture and services.
- Prioritize vulnerability exploitation.
An Example of a Pentest Using Python
Now that we have a clearer understanding of the what and why, let’s dive into an example of a Pentest using Python.
Let’s say we want to scan a network for open ports using the nmap library in Python.
Prerequisites
- Python installed on your machine
- Nmap installed on your machine
- Install the
python-nmaplibrary using pip:
pip install python-nmapPython Code Example
Here’s a simple Python script that uses the python-nmap library:
import nmap
def scan_open_ports(target_ip):
nm = nmap.PortScanner()
print(f"Scanning target: {target_ip}...\n")
nm.scan(target_ip, arguments='-sS -Pn') # TCP SYN scan, no ping
if nm.all_hosts():
for host in nm.all_hosts():
print(f"Host: {host} ({nm[host].hostname()})")
print(f"State: {nm[host].state()}")
for proto in nm[host].all_protocols():
lport = nm[host][proto].keys()
for port in sorted(lport):
print(f"Port: {port}\tState: {nm[host][proto][port]['state']}")
else:
print("No hosts found.")
if __name__ == "__main__":
target = input("Enter the target IP address or hostname: ")
scan_open_ports(target)
How to Use This Script
- Copy the code into a file named
port_scanner.py. - Run the script using the command:
- Copy the code into a file named
python port_scanner.py- Input the target IP address or hostname when prompted.
Example Output
When you run the script, you might see output similar to the following:
Enter the target IP address or hostname: 192.168.1.1
Scanning target: 192.168.1.1...
Host: 192.168.1.1 (router)
State: up
Port: 22 State: open
Port: 80 State: open
Port: 443 State: open
Important Notes
- Ensure you have permission to scan the target.
- Nmap must be installed and accessible in your system’s PATH.
- Some Nmap features require root privileges
Performing a penetration test using the Nmap library in Python involves utilizing python-nmap to scan networks, identify open ports, services, and potential vulnerabilities. Steps include installing python-nmap, importing the library, defining the target IP, configuring scan options, executing the scan, and parsing results. Various scan types are available, including TCP Connect, UDP, OS Detection, and Service Version Detection. Example code demonstrates how to scan a target IP, retrieve results, and parse findings.
What are the Benefits of Pentesting?
Pentesting offers numerous benefits to organizations, including:
- Improved Security Posture: Identifying vulnerabilities before attackers do.
- Reduced Risk: Minimizing potential breaches and data compromise.
- Compliance: Meeting regulatory requirements and avoiding fines.
- Cost Savings: Preventing costly breaches and downtime.
- Enhanced Incident Response: Developing effective response strategies.
- Better Resource Allocation: Prioritizing security efforts based on pentest findings.
- Increased Customer Trust: Demonstrating commitment to security and data protection
By incorporating pentesting, one can significantly improve his/her organization’s overall security posture and resilience.
Conclusion
Inn conclusion, pentesting is a vital component of a robust cybersecurity strategy. By understanding pentesting basics, types, and benefits, organizations can proactively strengthen their defenses, reduce risk, and protect sensitive data. Whether you’re a seasoned security professional or just starting out, pentesting is an essential tool in the fight against cyber threats.
References
Book A Free Security Consultation With SecureMyOrg!
SecureMyOrg is a reputable cybersecurity firm that has worked with renowned companies like Yahoo, Gojek and Rippling.
We build security for startups. If you’re someone looking for a trusted cybersecurity partner, feel free to reach out to us – LinkedIn or Email. Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.

Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.
